CISA Course Training Institute & Certification Exam Center
CISA Course Training Key Features
What our students talks about us. If you were student of WebAsha and wants to share your thought about us, kindly mail or call us.
Course Duration : 2 Months
Real Time Projects : 2
Hands-on Training
Full Day Lab Access
Certification & Job Assistance
Post Training Support
World's Biggest CISA Cloud Labs
Hands-on experience with real-world cloud environments to build job-ready skills.
24/7 access to cloud labs, enabling learning anytime, anywhere.
Zero downtime.
Practice across multiple cloud platforms, including AWS, Azure, and Google Cloud.
Instant scalability and resources to match real-world cloud infrastructure.
Expert-guided labs with industry-relevant scenarios for comprehensive learning.

CISA Training Classes Calender
| Start Date | Training Mode | Enroll Status |
|---|---|---|
|
May 03, 2025
10:00 - 13:00 (IST) |
Classroom/Online Weekdays/Weekend |
Enrollment Open |
|
May 11, 2025
13:00 - 16:00 (IST) |
Classroom/Online Weekdays/Weekend |
Enrollment Open |
|
Apr 23, 2025
14:00 - 17:00 (IST) |
Classroom/Online Weekdays/Weekend |
Enrollment Close |
Can’t find a batch you were looking for?
Classroom / Online CISA Course Training Overview
- Information Systems Audit Process: The course introduces the fundamental concepts of information systems auditing, including the audit planning process, scope and objectives of audits, and the importance of adherence to professional standards and ethics.
- Governance and Management of IT: This section focuses on understanding IT governance frameworks, IT strategy, policies, and standards. It covers topics such as IT organizational structure, roles, responsibilities, and the alignment of IT with business objectives.
- Information Systems Acquisition, Development, and Implementation: Participants learn about the processes and controls involved in the acquisition, development, and implementation of information systems. This includes topics like project management practices, system development methodologies, and system testing and validation.
- Information Systems Operations, Maintenance, and Service Management: This section covers the operational aspects of information systems, including system configuration and change management, incident management, and problem management. It also addresses the management of IT service delivery and support processes.
- Protection of Information Assets: Participants gain an understanding of the principles and practices of information security and risk management. Topics covered include access control systems and methodologies, network and infrastructure security, physical security, and data classification and protection.
- Audit and Assurance Practices: The course covers the audit process, audit planning and management, evidence collection, and the application of audit techniques and tools. It also explores the concepts of internal controls, control frameworks, and risk assessment methodologies.
- The Role of the CISA Professional: Participants learn about the responsibilities, skills, and competencies required of a Certified Information Systems Auditor. This includes topics such as professional ethics, professional development, and the role of IT auditors in the overall governance and risk management processes.
- IT Auditors: Professionals responsible for conducting independent audits of information systems to assess their controls, risks, and compliance with regulatory requirements.
- IT Security Professionals: Individuals involved in designing, implementing, and managing information security programs within organizations.
- IT Consultants: Professionals providing advisory services related to information systems auditing, control, and security to clients in various industries.
- Risk Management Professionals: Individuals responsible for assessing and managing information security risks within organizations.
- IT Governance Professionals: Professionals involved in establishing and maintaining IT governance frameworks and ensuring alignment between IT and business objectives.
Course Syllabus
| Topic | Details | Weights |
|---|---|---|
| INFORMATION SYSTEMS AUDITING PROCESS | - Providing audit services in accordance with standards to assist organizations in protecting and controlling information systems. Domain 1 affirms your credibility to offer conclusions on the state of an organization’s IS/IT security, risk and control solutions. A. Planning
B. Execution
| 21% |
| Governance and Management of IT | - Domain 2 confirms to stakeholders your abilities to identify critical issues and recommend enterprise-specific practices to support and safeguard the governance of information and related technologies. A. IT Governance
B. IT Management
| 17% |
| Information Systems Acquisition, Development and Implementation | A. Information Systems Acquisition and Development
B. Information Systems Implementation
| 12% |
| INFORMATION SYSTEMS OPERATIONS AND BUSINESS RESILIENCE | - Domains 3 and 4 offer proof not only of your competency in IT controls, but also your understanding of how IT relates to business. A. Information Systems Operations
B. Business Resilience
| 23% |
| Protection of Information Assets | - Cybersecurity now touches virtually every information systems role, and understanding its principles, best practices and pitfalls is a major focus within Domain 5. A. Information Asset Security and Control
B. Security Event Management
- Supporting Tasks
| 27% |
Note: **The topics said above are only the short blueprint of the syllabus. On the off chance that you feel that we have missed any subject, you can simply come to us and learn it, or simply call us to affirm
Call at 8010911256 | 8485846227 WebAsha Provides Best Online [Live Interactive Class] / Calssroom with practical based hands-on CISA Training and Certification in Pune and near by area. Get Course Details, Certification Cost, Fees, Syllabus, Duration, Batch Timings, Exam Preparation, workshops in Pune, Mumbai, Delhi NCR, Noida, Gurugram (Gurgaon), Hyderabad, Bengaluru (Bangalore), India, UK, USA, UAE, Dubai, Singapore, and Australia
Have An Queries? Ask our Experts
Help me to Choose a Course.
Mode of Training
CISA Classroom Training
- Interactive Learning: Participate in face-to-face sessions with experienced instructors, facilitating real-time interaction and immediate feedback.
- Hands-On Experience: Engage in practical exercises and lab sessions to enhance your hands-on skills.
- Collaborative Environment: Benefit from the collaborative environment where you can network and work with peers.
- State-of-the-Art Facilities: Access to advanced training facilities and resources.
Online CISA Training
- Flexible Schedule: Learn at your own pace from the comfort of your home or office, fitting the course around your personal and professional commitments.
- Live Sessions: Attend live, instructor-led sessions that provide the same quality of training as in the classroom.
- Accessibility: Access training materials and resources anytime, anywhere with a stable internet connection.
CISA Corporate Training
- Customized Content: : Tailored training programs designed to meet your organization’s specific needs and goals.
- On-Site Training:: Instructors can come to your business location, providing training in a familiar and convenient setting.
- Skill Enhancement:: Equip your team with the latest skills and knowledge to stay competitive in the industry.
- Team Building:: Foster a collaborative learning environment that promotes team building and knowledge sharing among employees.
- Flexible Delivery: : Options for both classroom and online training to suit your company’s schedule and preferences.
CISA Session Recordings
Whether you choose classroom, online, or corporate training, you will receive recordings of each session of CISA Course on our Learning Management System (LMS) . This allows you to:
- Revise at Your Convenience: Review the recorded sessions at any time to reinforce your understanding of the topics covered.
- Catch Up on Missed Content: If you miss a session, you can easily catch up by watching the recording.
- Flexible Learning: Revisit challenging concepts and sections as many times as needed, ensuring a thorough grasp of the material.
At WebAsha Technologies, we are committed to providing you with a seamless and effective and best learning experience of CISA Course, tailored to your needs and schedule.
Trainer Profile
- They have More than 10+ years of experience in Ethical Hacking and related technologies.
- Our Trainers are expert level and completely up-to- date in the subjects they teach because they continue to spend time working on real- world industry applications.
- Our Trainers have Experienced on multiple real- time Industries related projects
- He Trained more than 1000+ Students in a year.
- He's certified Professionals with High Grade
- Having Strong Theoretical & Practical Knowledge.
CISA Certification Bootcamp
CISA
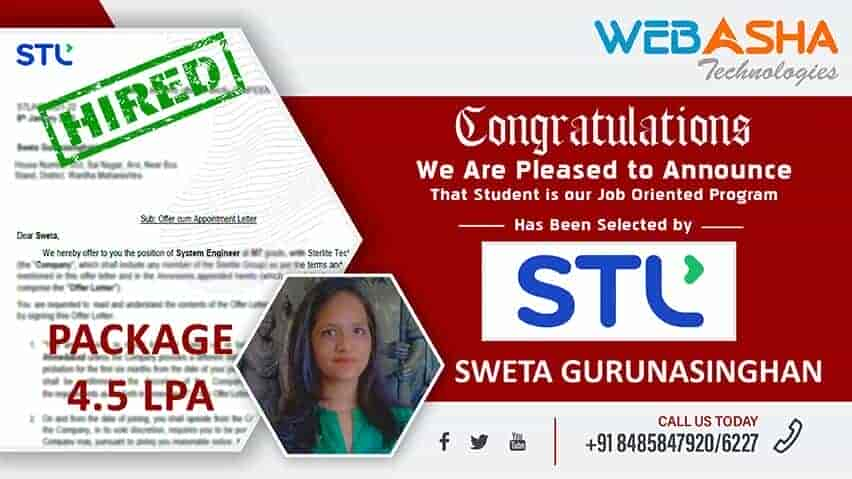
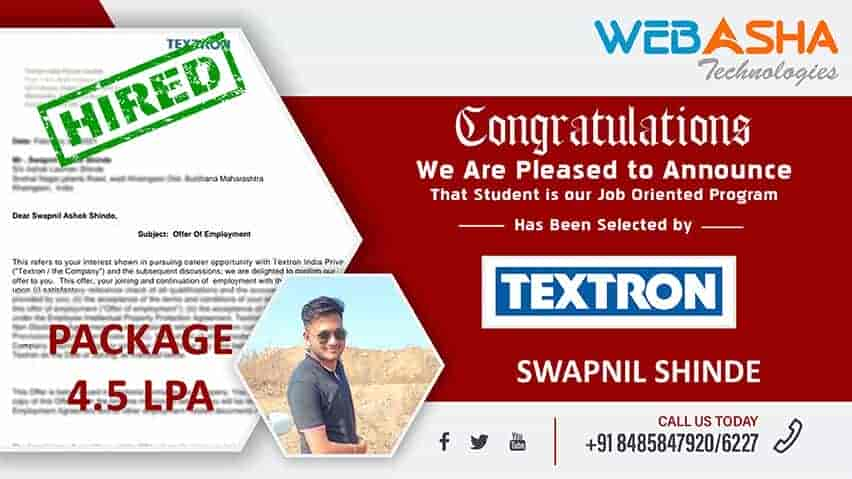
Our Recent Certified Candidates
Real Exam Format and Information
Passing Score of CISA Global Certification Exam
CISA Training & Global Certification Benefits | Job Profiles | Salary Range
- Enhanced Career Opportunities: CISA certification is highly valued and respected in the IT audit and cybersecurity industry. It can open up new job opportunities and increase your chances of securing positions such as IT auditor, information security manager, compliance officer, risk manager, and more.
- Global Recognition: CISA is recognized worldwide as a leading certification for IT auditors and security professionals. It demonstrates your competence and expertise in the field and enhances your professional credibility internationally.
- Industry Demand: With the increasing importance of information security and the growing number of cyber threats, there is a high demand for professionals who can assess and audit information systems effectively. Holding the CISA certification positions you as a qualified candidate for organizations seeking skilled individuals to ensure the security and integrity of their IT infrastructure.
- Knowledge and Skills: The CISA certification process requires candidates to acquire in-depth knowledge and skills in areas such as IT governance, risk management, information systems audit, and control. This knowledge equips you with a comprehensive understanding of auditing processes, controls, and security best practices, enabling you to provide valuable insights and recommendations to your organization.
- Professional Development: The CISA certification is not a one-time achievement. To maintain the certification, you need to adhere to ISACA's continuing professional education (CPE) requirements, which encourage ongoing learning and development. This helps you stay updated with the latest trends, technologies, and regulations in the field, ensuring your skills remain relevant and valuable.
- IT Auditor: Conducting audits of IT systems, assessing controls and risks, and providing recommendations for improvement.
- Information Security Manager: Overseeing the security of information systems, implementing controls, and managing incidents and vulnerabilities.
- Compliance Officer: Ensuring organizational compliance with relevant laws, regulations, and industry standards.
- Risk Manager: Identifying and assessing risks related to information systems, developing risk mitigation strategies, and monitoring risk levels.
- IT Consultant: Providing advisory services to organizations on IT governance, risk management, and compliance.
How does WebAsha Technologies Placement Work?
Mock Interviews
- Enhance your interview preparation and performance by participating in our Mock Interviews at WebAsha Technologies. Gain the confidence to excel in real-life job interviews with the guidance of our expert team.
- If you feel uncertain about interview environments, rest assured that our team will familiarize you with different scenarios, enabling you to showcase your skills under any level of pressure.
- Our Mock Interviews are conducted by industry experts who possess extensive years of experience. Their insights and expertise will significantly improve your chances of securing a job in the real world.

Projects
- Projects: Validate your skills and knowledge by working on industry-based projects that feature real-time use cases. Obtain hands-on expertise in top IT skills, becoming industry-ready through our project works and assessments.
- Our projects align perfectly with the curriculum's modules and are selected based on the latest industry standards. Enhance your resume with meaningful project work, capturing the attention of top industries and opening doors to lucrative salary opportunities.
- Join our Mock Interviews program today and elevate your interview skills to new heights, paving the way for a successful career.
To See thousands of 100% Genuine WebAsha Placement Testimonials
View all Placement TestimonialsCISA Recent Reviews
CISA Reviews
CISA FAQ
Carousel with controls
Most Demanded Course
Related Classes
Trending Courses
Our Recent Placement
What our students talks about us. If you were student of WebAsha and wants to share your thought about us, kindly mail or call us.
WebAsha FAQ(Frequently Asked Questions)
-
Why Should I Learn this Course from WebAsha Technologies in Pune?
-
Hey! Are You Looking for Exciting Offers?
-
Does WebAsha Technologies Offer Placement Assistance After Course Completion?
-
Who is My Trainer & How are they Selected?
-
What to Do if I Miss a Session?
-
Which type of Certification will I Receive After Course Completion?
-
Any Group Discounts (or) Corporate Training for Our Team?
-
What are the Payment Options?
-
Still, I have More Queries to Ask?
Our Learners Work at
Top Fortune 500 Company























Trusted by the best
Available Technologies