What Is the Certified Ethical Hacking - CEH v12 ?
CEH v12 is the industry's most comprehensive program, with training, certification, practice, engagement, and competition all wrapped into one course. This one-of-a-kind certification provides comprehensive training in ethical hacking with hands-on training, labs, assessments, mock engagements (practice), and global hacking competitions to ensure that students are at the top of their game.

1. What is Ethical Hacking?
Ethical hacking (EH) is any penetration testing done to test a system’s security readiness. The phrase “ethical” refers to the fact that EH doesn't involve breaking into someone else's computer system or network. Rather, it focuses on finding vulnerabilities in a company's own systems, and then fixing them before attackers do.
2. Why should you hack?
While it may seem counterintuitive to fix your own vulnerabilities, many hackers consider EH a valuable service. If a company’s systems have been breached, they can use an EH session to identify what went wrong so they aren't vulnerable again. In addition, companies can benefit from gaining a deeper understanding of their own networks and systems.
3. How much do you charge?
The price for an EH session varies depending on the scope of the problem, how long it takes to resolve the issue, and whether anything goes wrong along the way. But most companies pay between $300-$500 per hour for EH work. Companies often split these costs over several months or years, making the cost not only affordable, but manageable.
4. Where do you perform your tests?
Many hackers conduct EH sessions remotely using live-streaming software like OBS Studio. Others physically visit clients' offices to carry out the assessments. A hacker might even set up a VPN connection and log onto the target server via remote desktop protocol (RDP).
5. What kind of information do you collect?
Depending on the project, hackers can gather a variety of data. Most commonly, an EH session collects basic information about the target’s network infrastructure: IP addresses, domain names, operating system version, router settings, etc. Hackers can also look at HTTP and HTTPS traffic, databases, email messages, and Web servers. And if the client wants, hackers can take screenshots of everything while they're working.
6. What happens after you finish the assessment?
After the assessment, hackers send clients an invoice detailing the findings. Many people don’t realize that EH isn't just about identifying potential targets; it's also about proving that the attacker was legitimate and that nothing bad happened. When a hacker sends invoices, he provides proof that he didn't gain access to any sensitive files or systems. He shows that he hasn't changed any passwords, deleted any records, or tampered with anything. If clients are satisfied with the results, they can pay their invoice and move forward with fixing the issues identified during the assessment.
7. Should I get certified?
If you want to earn extra money, becoming a Certified Ethical Hacker (CEH v12) could give you some added credibility when talking to potential customers. But because CEH doesn't require specific skills or training, anyone can become certified.
CEH v12 Introducing the All-New Learning Framework
- LEARN
- CERTIFY
- ENGAGE
- COMPETE
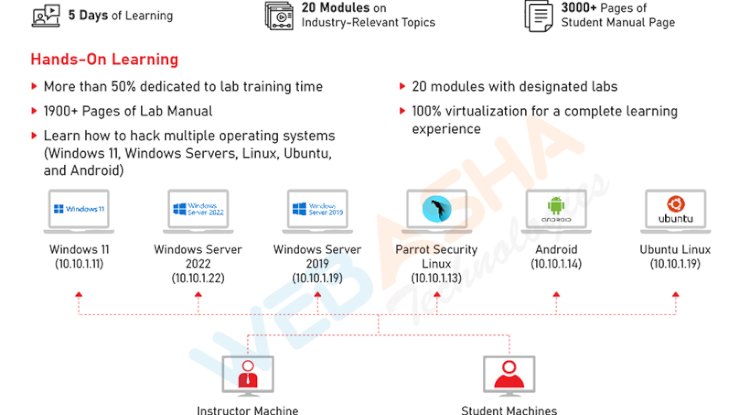
1. CEH v12 LEARN
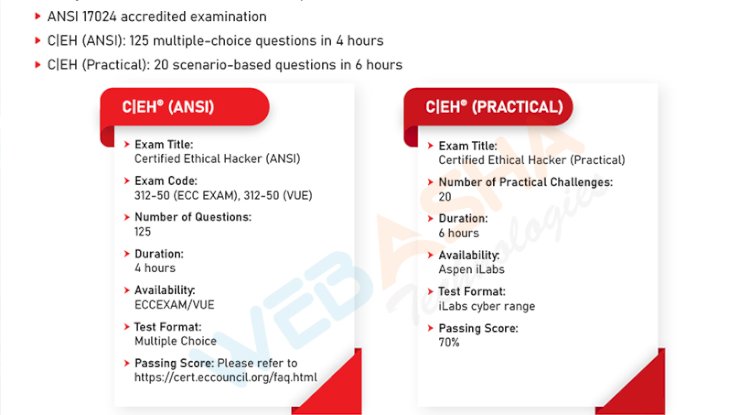
2. CEH v12 CERTIFY
3. CEH v12 ENGAGE
4. CEH v12 COMPETE











![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)

![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)









