Step-by-Step Guide to OWASP ZAP for Vulnerability Testing
Explore the world of web application security with OWASP ZAP, the powerful open-source tool for vulnerability testing. This comprehensive guide walks you through installation, testing techniques, managing alerts, and generating detailed reports. Perfect for beginners and professionals alike, with step-by-step instructions and visual aids to make your testing efficient and effective.

Web application security is critical for safeguarding user data and maintaining trust. One of the most powerful tools for testing web application vulnerabilities is OWASP ZAP (Zed Attack Proxy). This guide will walk you through its features, how to test a website, and generate reports while highlighting where to include images for better illustration.
What is OWASP ZAP?
OWASP ZAP is an open-source security testing tool used for detecting vulnerabilities in web applications. Developed by the Open Web Application Security Project (OWASP), it is one of the most popular tools for penetration testing.
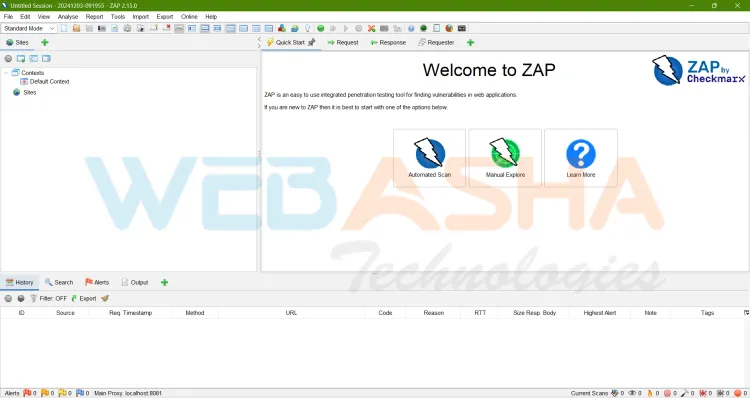
Why Use OWASP ZAP?
- Free and Open Source: Accessible to anyone, including individual developers and organizations.
- Powerful Automation: Includes an automated scanner for quick testing.
- Manual Testing Capabilities: Offers in-depth tools like intercepting proxy, spider, and fuzzers.
- Beginner-Friendly: Easy to use, even for those new to security testing.
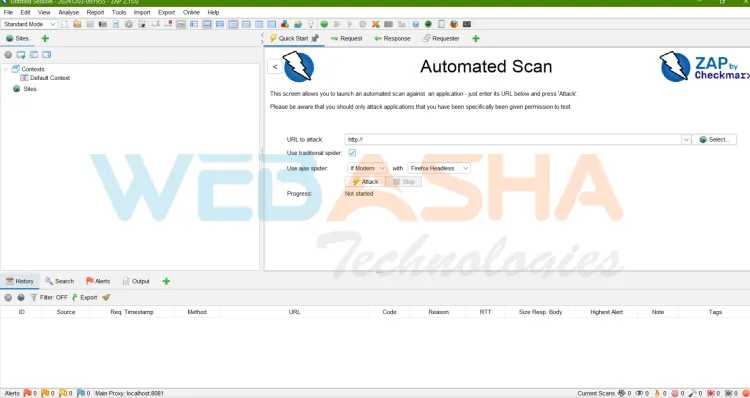
Getting Started with OWASP ZAP
Installation
- Download OWASP ZAP from the official website.
- Install it on your system (supports Windows, macOS, and Linux).
How to Test a Website Using OWASP ZAP
Step 1: Configure ZAP as a Proxy
Launch ZAP and configure your browser to route traffic through ZAP’s proxy.
-
- Default address:
127.0.0.1 - Default port:
8080
- Default address:
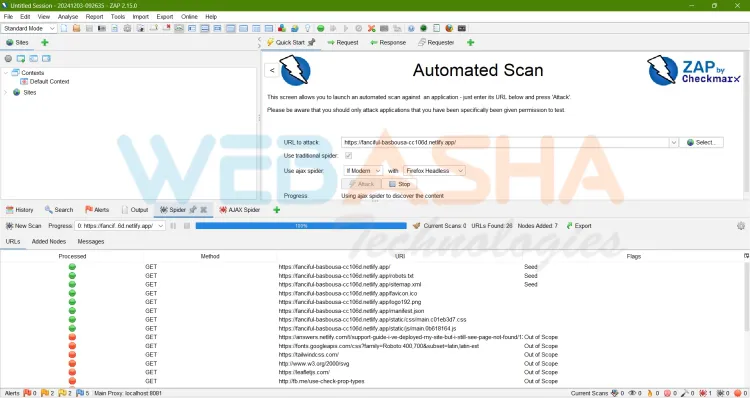
Step 2: Spider the Target Website
- Enter the target URL in the Quick Start tab.
- Select the Spider option to crawl the entire website.
- ZAP will map all pages and endpoints for further testing.
Step 3: Run Active Scan
- After the Spider completes, right-click the target in the left-hand tree view.
- Select Attack > Active Scan.
- Monitor the scan progress in the bottom panel.
Understanding and Managing Alerts
What Are Alerts?
After scanning, ZAP generates alerts for detected vulnerabilities, categorizing them by severity:
- High: Critical issues needing immediate attention.
- Medium: Moderate vulnerabilities.
- Low: Minor issues.
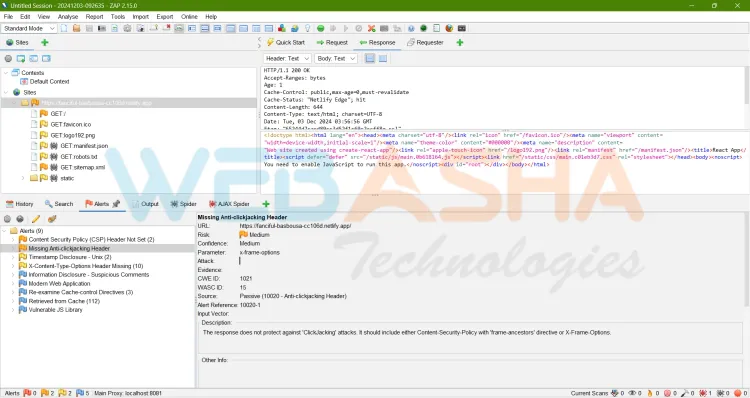
How to View Alerts
- Navigate to the Alerts tab at the bottom panel.
- Click on individual alerts for detailed information, including:
- Description: Explains the vulnerability.
- Solution: Suggests remediation steps.
- Reference: Provides links to relevant resources.
Fixing Vulnerabilities
- Analyze the suggested solutions.
- Prioritize fixes based on severity.
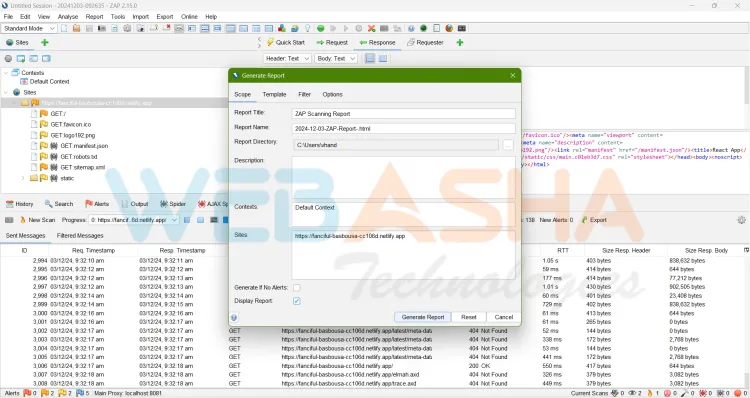
Generating Reports in ZAP
Steps to Generate a Report
- Navigate to Report > Generate HTML Report from the top menu.
- Save the report to your desired location.
- The report will include details of all vulnerabilities detected during the scan.
What to Include in the Report?
- Overview of vulnerabilities.
- Detailed information for each alert.
- Risk levels (High, Medium, Low).
Tips for Using OWASP ZAP Effectively
- Combine Scans: Use both automated and manual scans for comprehensive results.
- Test Regularly: Regular scans ensure newly introduced vulnerabilities are caught.
- Leverage Plugins: Extend ZAP's functionality using its add-on marketplace.
- Integrate with CI/CD: Automate testing in your DevOps pipeline for continuous monitoring.
Conclusion
OWASP ZAP is an indispensable tool for web application security testing. Its powerful features, user-friendly interface, and extensive community support make it a favorite among security professionals. By learning to use ZAP effectively, you can identify and mitigate vulnerabilities, ensuring robust application security.
FAQ:
1. What is OWASP ZAP?
OWASP ZAP (Zed Attack Proxy) is an open-source tool used for security testing of web applications, developed by the OWASP community.
2. Who can use OWASP ZAP?
OWASP ZAP is designed for everyone, from beginners to advanced penetration testers and developers looking to secure their web applications.
3. What operating systems does ZAP support?
OWASP ZAP supports Windows, macOS, and Linux.
4. How does OWASP ZAP detect vulnerabilities?
ZAP detects vulnerabilities through automated scanning and manual tools like spiders, intercepting proxies, and fuzzers to analyze application behavior.
5. Is OWASP ZAP free to use?
Yes, OWASP ZAP is completely free and open-source, making it accessible to individuals and organizations of any size.
6. What types of vulnerabilities can ZAP identify?
OWASP ZAP can detect a wide range of vulnerabilities, including SQL injection, XSS (Cross-Site Scripting), broken authentication, and more.
7. Can ZAP be integrated into CI/CD pipelines?
Yes, ZAP supports integration into CI/CD pipelines, enabling automated vulnerability testing during development and deployment stages.
8. How do I generate a report in OWASP ZAP?
To generate a report, go to Report > Generate HTML Report, and save it. The report includes details of all identified vulnerabilities, categorized by severity.
9. What is the difference between an Active Scan and a Passive Scan?
- Active Scan: Actively interacts with the application, sending attack payloads to test vulnerabilities.
- Passive Scan: Analyzes traffic without interacting or altering the application.
10. How can I fix vulnerabilities identified by ZAP?
ZAP provides suggested solutions for each detected vulnerability in the Alerts tab. Prioritize fixes based on severity and consult the provided references for detailed remediation.











![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)



![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)







