PUMAKIT Linux Rootkit | A New Threat That Hides in Plain Sight
PUMAKIT Linux Rootkit is a newly discovered, sophisticated malware targeting Linux systems. This stealthy rootkit integrates into the Linux kernel as a Loadable Kernel Module (LKM), using advanced techniques like system call hooking, privilege escalation, memory-resident execution, and conditional activation to remain undetected. It operates through multiple components, including a dropper, kernel module, and userland rootkit, hiding files, escalating privileges, and executing malicious tasks. Researchers from Elastic Security Labs identified PUMAKIT in September 2024, highlighting its complexity and the growing threat of Linux-targeted malware. To combat such threats, users are advised to regularly update systems, monitor activity, restrict access, and deploy advanced security tools.

The world of cybersecurity is ever-evolving, with new threats emerging every day. One of the latest and most sophisticated threats is the PUMAKIT Linux Rootkit. This dangerous malware targets Linux systems and has been designed to operate in stealth, making it incredibly difficult to detect. In this blog, we will explore what PUMAKIT is, how it works, and what makes it a serious concern for Linux users.
What is PUMAKIT?
The PUMAKIT Linux Rootkit is a highly advanced piece of malware with the following goals:
- Escalating privileges: Gaining unauthorized access to system-level controls.
- Hiding itself: Making it almost invisible to security tools.
- Performing malicious actions: Such as data theft or system manipulation.
It functions as a Loadable Kernel Module (LKM), which allows it to integrate with the Linux kernel (the operating system's core) and alter how the system operates.
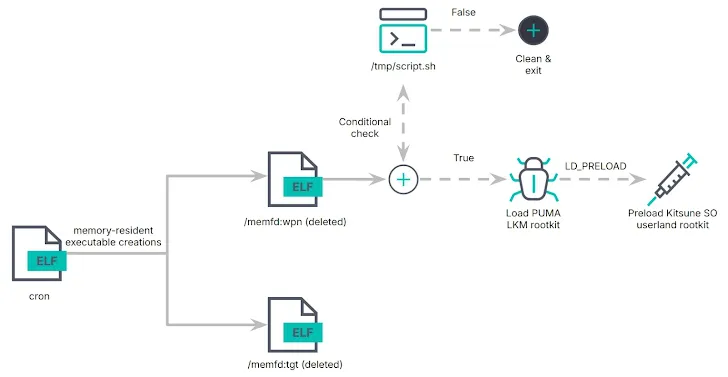
How Does PUMAKIT Work?
The PUMAKIT Linux Rootkit follows a multi-stage process to carry out its activities while staying hidden from detection. Here's an overview of its operation:
1. The Dropper
The malware begins with a dropper file named "cron". Its job is to plant the other components of the malware on the infected system.
2. Memory-Resident Executables
Two files, "/memfd:tgt" and "/memfd:wpn", are loaded into the system's memory. These files don't leave traces on the disk, making detection very challenging.
"/memfd:tgt"is a disguised Linux Cron binary."/memfd:wpn"is a loader that activates the rootkit when conditions are met.
3. LKM Rootkit
The core of the malware is a kernel module called "puma.ko". This module enables the malware to:
- Hide files and directories.
- Escalate its privileges.
- Execute malicious actions while remaining undetected.
4. Userland Rootkit
A library named "libs.so", also referred to as Kitsune, works in the user space. It acts as a bridge between the rootkit and attackers, enabling additional operations.
Techniques Used by PUMAKIT
The PUMAKIT Linux Rootkit employs advanced techniques to maintain its stealth and achieve its objectives. These include:
1. System Call Hooking
PUMAKIT modifies up to 18 system calls, allowing it to manipulate system functions and hide its presence.
2. Privilege Escalation
By exploiting kernel functions like "prepare_creds" and "commit_creds", it grants itself elevated privileges, bypassing security barriers.
3. Conditional Activation
The malware activates only under specific conditions, such as:
- Systems with secure boot vulnerabilities.
- Presence of certain kernel symbols.
This selective activation helps avoid detection during regular scans.
4. Memory-Resident Execution
Parts of the malware are loaded directly into memory. This approach eliminates disk traces, making it hard for traditional antivirus tools to detect.
5. Unique Commands
PUMAKIT uses unconventional methods, such as repurposing the rmdir() command to escalate privileges or extract data.
Why is PUMAKIT Dangerous?
The PUMAKIT Linux Rootkit is a significant threat for several reasons:
- Stealth: It integrates with the kernel and resides in memory, making it nearly invisible.
- Complexity: Its sophisticated design reflects the expertise of its creators.
- Anonymity: It hasn’t been linked to any known cybercriminal groups, complicating attribution.
Who Discovered PUMAKIT?
This rootkit was identified by Elastic Security Labs, whose researchers analyzed malware samples uploaded to VirusTotal in September 2024. Their findings highlight the advanced techniques used in PUMAKIT, setting it apart from other Linux threats.
How to Protect Against PUMAKIT
While PUMAKIT is challenging to detect, there are several steps users can take to safeguard their Linux systems:
- Regular Updates: Keep your systems up-to-date with the latest security patches.
- Advanced Security Tools: Use tools that monitor kernel behavior and memory activities.
- Access Restrictions: Limit who can load kernel modules or make system changes.
- System Monitoring: Watch for unusual activities, like unexpected privilege escalations or hidden processes.
Conclusion
The discovery of the PUMAKIT Linux Rootkit underscores the increasing sophistication of threats targeting Linux systems. Its ability to evade detection and execute advanced attacks makes it a formidable adversary. However, with proactive measures, such as regular updates and advanced monitoring tools, its impact can be minimized.
As cybersecurity threats continue to evolve, staying informed and vigilant is the key to defending against attacks like PUMAKIT. Ensure you take every precaution to protect your Linux systems from this and other advanced malware.
FAQ:
1. What is PUMAKIT?
PUMAKIT is a stealthy Linux rootkit designed to hide in the system and perform malicious activities like privilege escalation and file hiding.
2. How does PUMAKIT operate?
It uses a multi-stage approach involving a dropper, memory-resident files, a kernel module, and a userland rootkit to execute its tasks.
3. What is the role of the dropper in PUMAKIT?
The dropper, named "cron", plants the malware on the system and initiates further stages of the attack.
4. How does PUMAKIT remain hidden?
It hooks system calls, executes in memory, and activates only under specific conditions, avoiding detection by traditional tools.
5. What are the key components of PUMAKIT?
The main components are the dropper ("cron"), memory-resident executables ("memfd:tgt" and "memfd:wpn"), the kernel module ("puma.ko"), and the userland library ("libs.so").
6. Who discovered PUMAKIT?
Researchers from Elastic Security Labs uncovered the rootkit in September 2024 through samples uploaded to VirusTotal.
7. What techniques does PUMAKIT use?
It employs system call hooking, privilege escalation, memory-resident execution, and conditional activation to evade detection.
8. Why is PUMAKIT dangerous?
Its ability to stay undetected, complexity, and potential for widespread exploitation make it a significant cybersecurity threat.
9. How can Linux users protect against PUMAKIT?
By keeping systems updated, using advanced security tools, monitoring activity, and restricting kernel module access.
10. What makes PUMAKIT unique?
Its advanced design, including conditional activation and memory-resident execution, sets it apart from typical Linux malware.











![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)



![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)







