Password Cracking with Hashcat: Techniques and Best Practices
Hashcat is a powerful and versatile password cracking tool designed for cybersecurity professionals to assess and strengthen password security. It supports a wide range of hash types and offers multiple attack modes, including dictionary, brute-force, and hybrid attacks, utilizing CPU and GPU hardware acceleration. It is widely used by penetration testers, security researchers, and forensic analysts for efficient password recovery. By mastering Hashcat’s commands and performance optimization techniques, users can crack various password hashes and ensure the security of their systems while adhering to ethical guidelines.

In the realm of cybersecurity and ethical hacking, password cracking is a critical skill for assessing the strength of passwords. Hashcat is one of the most powerful and versatile tools available for this purpose. In this guide, we’ll explore what Hashcat is, how it works, and provide a comprehensive list of its commands and use cases.
What is Hashcat?
Hashcat is a robust, fast, and highly optimized password recovery tool capable of cracking various hash types. It supports CPUs, GPUs, and other hardware accelerators to perform brute-force and dictionary attacks efficiently. Hashcat is designed for penetration testers, security researchers, and forensic analysts to evaluate password security.
Features of Hashcat:
- Supports over 300 hash types (e.g., MD5, SHA family, bcrypt, NTLM).
- Highly optimized for modern CPUs and GPUs.
- Provides multiple attack modes.
- Allows distributed cracking across multiple devices.
- Open-source and community-driven.
Installing Hashcat
Hashcat comes pre-installed in many penetration testing distributions like Kali Linux. For other platforms, follow the steps below:
On Linux:
sudo apt update
sudo apt install hashcat
On macOS (using Homebrew):
brew install hashcat
On Windows:
- Download the binary from the official Hashcat website.
- Extract the archive and use the hashcat.exe file.
Key Hashcat Concepts
Hashes
A hash is a fixed-length string generated from input data (e.g., passwords). Hashes are used for storing sensitive information securely, but they can be cracked using tools like Hashcat.
Attack Modes
Hashcat offers several attack modes to adapt to different scenarios:
- Straight Attack (-a 0): Uses a wordlist to try password combinations.
- Combination Attack (-a 1): Combines words from two wordlists.
- Brute-force Attack (-a 3): Attempts every possible character combination.
- Hybrid Attack (-a 6 or -a 7): Combines a wordlist with brute force.
Hash Types
Hashcat supports a wide range of hash types, including:
- MD5 (-m 0)
- SHA-1 (-m 100)
- NTLM (-m 1000)
- bcrypt (-m 3200)
- SHA-256 (-m 1400)
Hashcat Command Syntax
The basic syntax for Hashcat is:
hashcat [options] -a -m
Common Hashcat Commands
1. Basic Dictionary Attack
Crack an MD5 hash using a wordlist:
hashcat -a 0 -m 0 hash.txt /usr/share/wordlists/rockyou.txt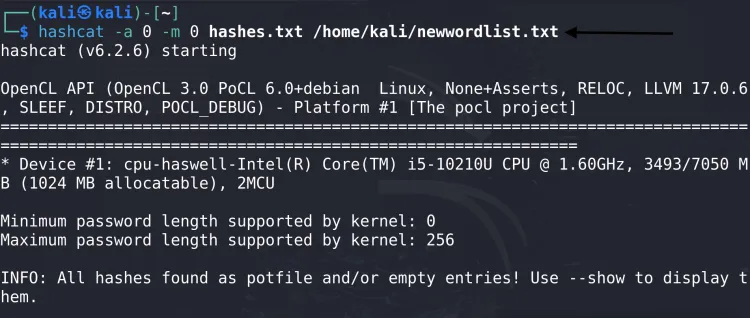
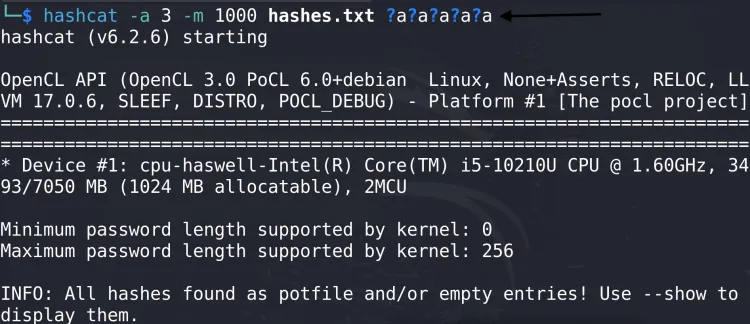
2. Brute-force Attack
Crack an NTLM hash with a brute-force attack:
hashcat -a 3 -m 1000 hash.txt ?a?a?a?a?a
Here, ?a represents all possible characters (lowercase, uppercase, numbers, and symbols).

3. Combination Attack
Combine two wordlists to generate candidate passwords:
hashcat -a 1 -m 0 hash.txt wordlist1.txt wordlist2.txt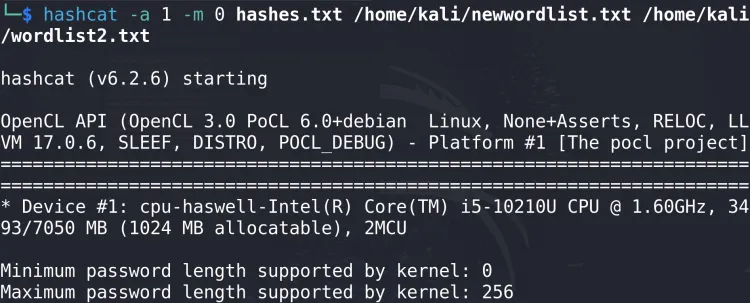

4. Hybrid Attack
Append characters to words from a wordlist:
hashcat -a 6 -m 0 hash.txt /usr/share/wordlists/rockyou.txt ?d?d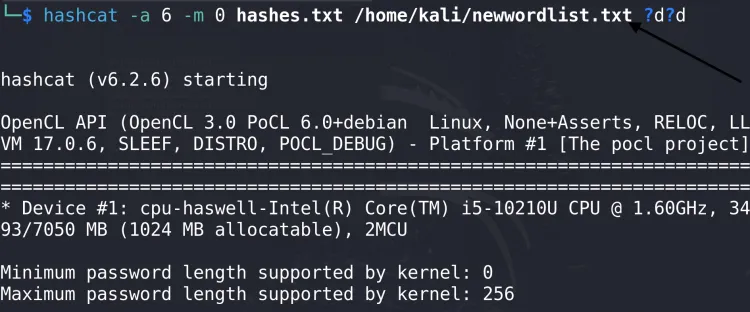

Prepend characters to words from a wordlist:
hashcat -a 7 -m 0 hash.txt ?d?d /usr/share/wordlists/rockyou.txt
5. Mask Attack
Specify a mask for custom character sets:
hashcat -a 3 -m 0 hash.txt ?l?u?d?s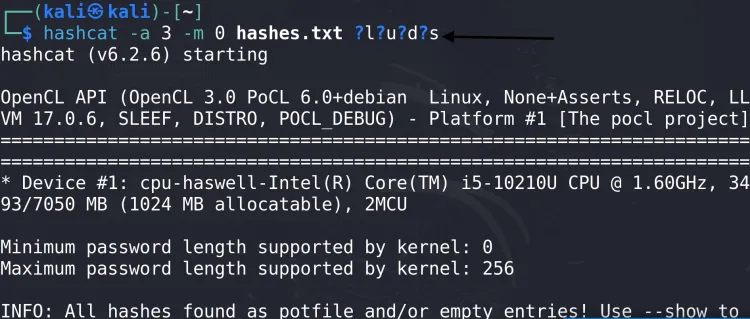

Where:
?l: Lowercase letters?u: Uppercase letters?d: Digits?s: Symbols
6. Using Rules
Rules modify wordlist entries dynamically:
hashcat -a 0 -m 0 hash.txt /usr/share/wordlists/rockyou.txt -r rules/best64.rule
7. Crack ZIP Passwords
Crack a ZIP file hash:
zip2john secured.zip > zip.hash
hashcat -a 0 -m 13600 zip.hash /usr/share/wordlists/rockyou.txt
8. Resume Cracking
If cracking is interrupted, resume with:
hashcat --session=my_session --restore
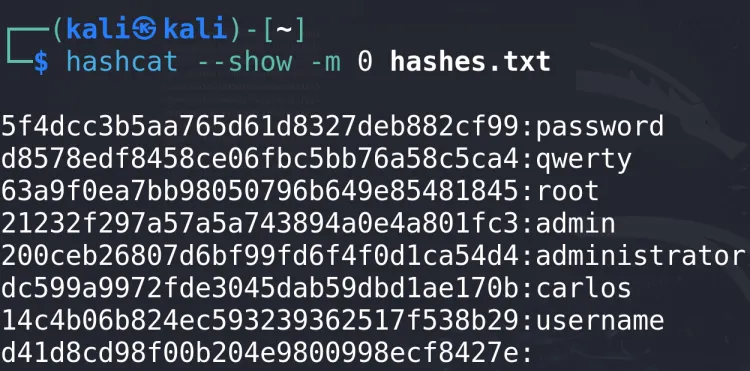
9. Show Cracked Passwords
To display already cracked passwords:
hashcat -m 0 hash.txt --show
10. Benchmark Performance
Test your system’s performance:
hashcat -b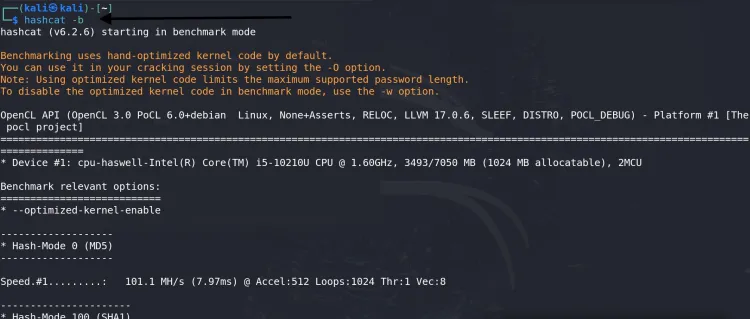
Optimizing Hashcat Performance
1. Hardware Acceleration
Hashcat supports GPUs for faster cracking. Use the -d option to specify devices:
hashcat -a 0 -m 0 hash.txt /usr/share/wordlists/rockyou.txt -d 1
2. Tuning Parameters
Adjust workload profiles for better performance:
hashcat -a 0 -m 0 hash.txt /usr/share/wordlists/rockyou.txt --optimized-kernel-enable
3. Utilize Rules
Enhance cracking efficiency with prebuilt rules:
hashcat -a 0 -m 0 hash.txt /usr/share/wordlists/rockyou.txt -r rules/best64.rule
Tips and Best Practices
- Know the Hash Type: Use tools like hashid or hash-identifier to identify the hash type.
- Use a Powerful GPU: GPU acceleration drastically improves cracking speed.
- Wordlist Management: Use large, curated wordlists like RockYou for better success rates.
- Distributed Cracking: Leverage multiple systems for faster results using distributed setups like Hashtopolis.
- Ethical Use Only: Ensure you have permission before attempting to crack passwords.
Conclusion
Hashcat is a must-have tool for cybersecurity professionals, offering unmatched speed and versatility in password cracking. By mastering its commands and techniques, you can evaluate and strengthen password security effectively. Always use Hashcat responsibly and adhere to ethical guidelines.
For more details and updates, visit the official Hashcat website.
FAQ:
1. What is Hashcat?
Hashcat is an advanced password cracking tool used by cybersecurity professionals to recover passwords from hashed data.
2. Which hash types are supported by Hashcat?
Hashcat supports over 300 hash types, including MD5, SHA-1, NTLM, bcrypt, and SHA-256.
3.How does Hashcat work?
Hashcat uses different attack modes, such as dictionary, brute-force, and hybrid attacks, and can leverage CPUs and GPUs for efficient cracking.
4. Is Hashcat free?
Yes, Hashcat is open-source and free to use.
5. Can Hashcat crack encrypted ZIP files?
Yes, Hashcat can be used to crack ZIP file passwords using the zip2john method.
6. What is the difference between a dictionary attack and a brute-force attack?
A dictionary attack uses a predefined list of words to guess the password, while a brute-force attack attempts every possible combination of characters.
7. How do I install Hashcat on Linux?
You can install Hashcat on Linux with the command sudo apt install hashcat.
8. What are some performance optimization techniques for Hashcat?
Use GPU acceleration, optimize workload profiles, and utilize rules to improve cracking efficiency.
9. Can Hashcat crack passwords from online services?
Hashcat can crack passwords if you have the hash, but ethical and legal boundaries must always be respected.
10. How can I resume a password cracking session in Hashcat?
You can resume a session with the command hashcat --session=my_session --restore.











![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)



![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)







