Mastering Burp Suite: A Step-by-Step Guide to Ethical Brute Force Testing
This blog provides a step-by-step guide on performing a brute force attack using Burp Suite on an intentionally vulnerable website for educational purposes. It explains the setup, capturing login requests, configuring payloads, launching the attack, and analyzing results, emphasizing the importance of ethical practices. Additionally, it outlines mitigation techniques like implementing account lockout policies, using CAPTCHA, enforcing strong passwords, and monitoring login attempts to protect against such attacks, while stressing the need for legal and responsible application of hacking skills.

Introduction
A brute force attack involves systematically trying all possible combinations of usernames and passwords to gain unauthorized access. Burp Suite, a powerful tool for web application security testing, simplifies this process with its Intruder module.
In this guide, we’ll demonstrate how to perform a brute force attack on a sample vulnerable site: http://testphp.vulnweb.com. This is a legal target provided by Acunetix for learning purposes.
Prerequisites
-
Burp Suite: Ensure it is installed on your system.
-
Web Browser: Set up to work with Burp Suite (e.g., Firefox or Chrome).
-
Proxy Configuration: Configure your browser to route traffic through Burp Suite’s proxy.
Step-by-Step Procedure
Step 1: Setting Up Burp Suite
-
Open Burp Suite and navigate to the Proxy tab.
-
Under Options, ensure the proxy listener is active on 127.0.0.1:8080.
-
Configure your browser to use this proxy:
-
For Firefox:
-
Go to
Settings > Network Settings > Manual Proxy Configurationand set HTTP Proxy to 127.0.0.1 and Port to 8080.
-
-
For Chrome:
-
Use an extension like SwitchyOmega to configure the proxy.
-
-
-
Test the setup by visiting any website in your browser. Ensure traffic appears in the HTTP history of Burp Suite’s Proxy tab.
Step 2: Capturing the Login Request
-
In your browser, visit http://testphp.vulnweb.com/login.php.
-
Enter any username and password in the login form (e.g.,
test/test) and submit it.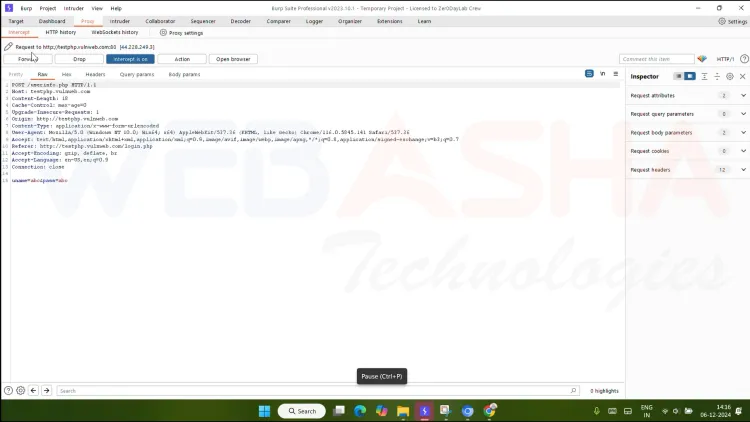
-
Switch to Burp Suite and navigate to the HTTP history in the Proxy tab.
-
Locate the intercepted login request and right-click > Send to Intruder.
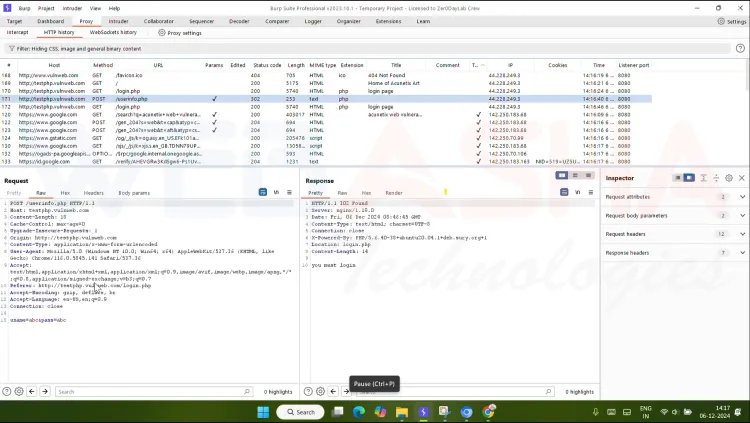
Step 3: Configuring Burp Suite Intruder
-
Go to the Intruder tab and select the attack you just sent.
-
In the Positions tab:
-
Clear all pre-selected fields by clicking Clear.
-
Highlight the username and password fields in the request and click Add to mark them as positions.
-
Example:
POST /login.php HTTP/1.1 Host: testphp.vulnweb.com Content-Type: application/x-www-form-urlencoded username=§admin§&password=§password§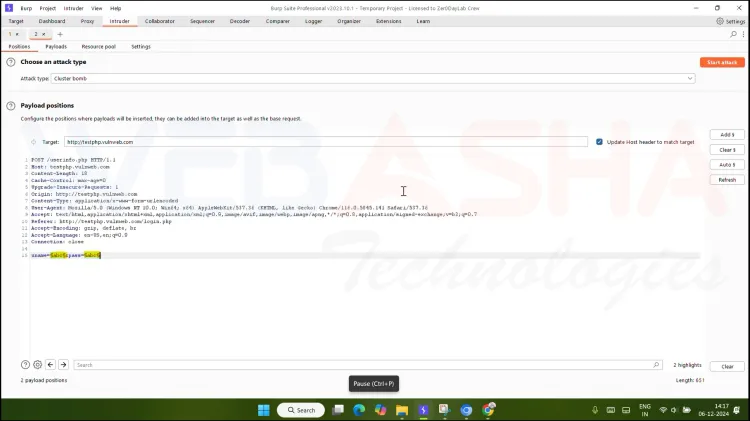
-
-
In the Attack Type, select Cluster Bomb.
Step 4: Adding Payloads
-
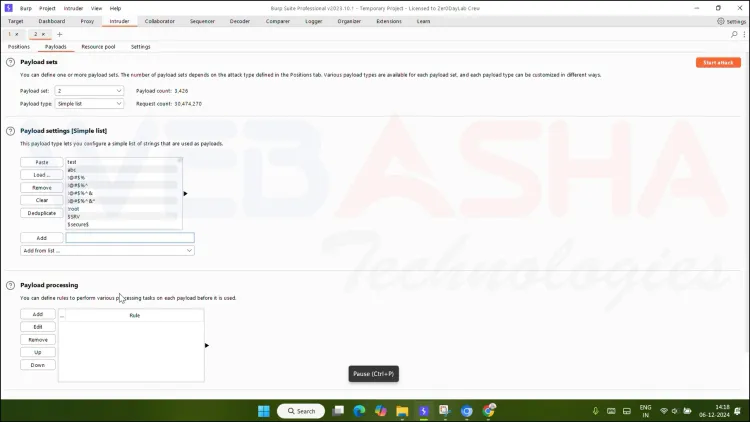
Go to the Payloads tab:
-
For the first position (username), add a list of potential usernames (e.g.,
admin,test,user). -
For the second position (password), add a list of common passwords (e.g.,
12345,password,admin).
-
-
You can either manually input these lists or load them from a file.
Step 5: Launching the Attack
-
Click Start Attack.
-
Burp Suite will systematically try each combination of usernames and passwords.
-
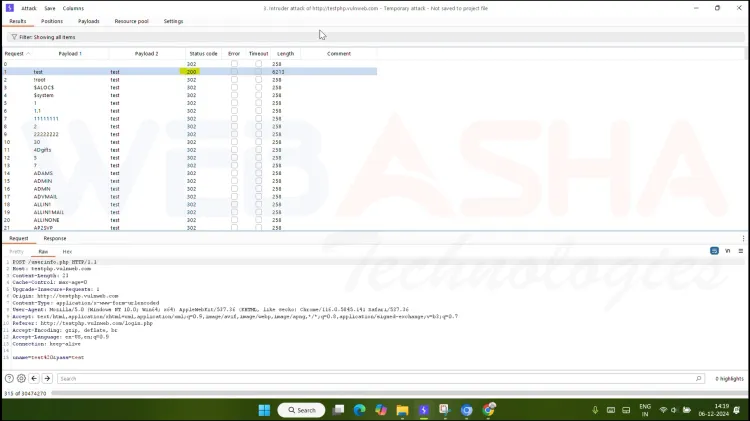
Monitor the Length column in the results:
-
Successful login attempts often have a different response length compared to failed attempts.
-
Step 6: Analyzing Results
-
Identify the successful login combination by analyzing:
-
Response Length: If the typical failed login responses are 200 bytes and one result is 350 bytes, the latter may indicate success.
-
HTTP Status Code: Successful logins might return a different status (e.g.,
200 OKor302 Found).
-
-
Note down the username and password pair used in the successful attempt.
Mitigation Techniques
Organizations can protect against brute force attacks by:
-
Implementing Account Lockout: Lock accounts after several failed login attempts.
-
Using CAPTCHA: Require human verification for login.
-
Enforcing Strong Passwords: Use complex passwords that are difficult to guess.
-
Monitoring Login Attempts: Track and block suspicious login attempts.
Legal and Ethical Considerations
-
Always obtain explicit permission before testing any website or application.
-
Unauthorized brute force attacks are illegal and can result in severe consequences.
-
Use ethical hacking skills responsibly to improve security, not exploit vulnerabilities.
Conclusion
This tutorial demonstrated how to use Burp Suite to perform a brute force attack on a vulnerable site. Such exercises are essential for understanding the security gaps in web applications and learning how to mitigate them effectively. Always practice ethical hacking responsibly and only on authorized systems.
Disclaimer: This guide is for educational purposes only. Unauthorized penetration testing or hacking is illegal. Perform such activities only in controlled environments or with explicit permission.
FAQ:
1. What is a brute force attack?
A brute force attack is a method used to gain unauthorized access to a system by systematically trying all possible combinations of usernames and passwords until the correct one is found.
2. What is Burp Suite?
Burp Suite is a powerful web application security testing tool used by ethical hackers and security professionals for tasks such as vulnerability scanning, brute force attacks, and other penetration testing activities.
3. Is it legal to perform brute force attacks?
Performing brute force attacks is illegal unless you have explicit permission from the system owner or are working on authorized platforms for educational or professional purposes.
4. Why is http://testphp.vulnweb.com used for this tutorial?
This site is a deliberately vulnerable application provided by Acunetix for ethical hacking practice and learning purposes.
5. How does Burp Suite help in brute force attacks?
Burp Suite\u2019s Intruder module automates the process of testing multiple username and password combinations efficiently, helping users analyze vulnerabilities in login mechanisms.
6. What is the purpose of proxy configuration in this setup?
The proxy configuration ensures that all web traffic from your browser is routed through Burp Suite, allowing it to capture and modify HTTP requests and responses.
7. How can organizations protect against brute force attacks?
Organizations can implement account lockout policies, use CAPTCHA, enforce strong password policies, monitor login attempts, and deploy multi-factor authentication to protect against brute force attacks.
8. What are common signs of a successful brute force attack?
A successful brute force attack often results in different HTTP response lengths or status codes, such as a redirect or access to restricted areas.
9. What should I do if I accidentally perform a brute force attack on an unauthorized system?
Immediately stop the attack, report the incident to the system owner, and explain the mistake. Seek legal advice if necessary to mitigate potential consequences.
10. Can I use this tutorial on live production systems?
No, this tutorial is strictly for educational purposes on authorized platforms. Testing on live systems without permission is unethical and illegal.











![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)



![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)







