Discover Hidden Web Paths: How to Use DirBuster for Security Assessments
DirBuster is a robust tool used in Kali Linux for ethical hacking and penetration testing, designed to uncover hidden directories and files on web servers that could reveal sensitive information or vulnerabilities. With features like customizable wordlists, recursive scanning, file extension targeting, and both GUI and CLI modes, it is versatile and user-friendly. Installation involves updating the system and running simple commands, while its usage includes selecting a target URL, choosing wordlists, and configuring options to perform scans. Adhering to ethical practices and combining DirBuster with tools like Burp Suite and Nmap can enhance security testing, making it a vital asset for identifying risks in web applications. DirBuster is a robust tool used in Kali Linux for ethical hacking and penetration testing, designed to uncover hidden directories and files on web servers that could reveal sensitive information or vulnerabilities. With features like customizable wordlist

DirBuster is a powerful and versatile tool used for brute-forcing web directories and files on web servers. It is particularly useful for ethical hackers and penetration testers to uncover hidden files and directories that may not be immediately visible through standard web browsing. Developed as part of the OWASP (Open Web Application Security Project) suite, DirBuster is widely used in Kali Linux, a popular penetration testing distribution.
In this blog, we will dive into the details of DirBuster, its purpose, and a step-by-step guide from installation to the scanning phase
Why Use DirBuster?
Web servers often have hidden directories and files that could expose sensitive information or lead to vulnerabilities. These directories might not be listed in the publicly accessible areas of the website but can still be accessed if their paths are known. DirBuster helps identify these hidden paths by brute-forcing the server using wordlists, making it a critical tool in identifying potential security loopholes.
Key Features of DirBuster
-
Customizable Wordlists: Supports multiple wordlists for effective brute-forcing.
-
Recursive Scanning: Automatically scans subdirectories.
-
File Extension Support: Can scan for specific file extensions.
-
User-Friendly Interface: Includes a GUI for easy operation.
Installation of DirBuster on Kali Linux
Kali Linux often comes pre-installed with DirBuster. However, if it is not available on your system, you can install it using the following steps:
Step 1: Update Your System
Before installing any tool, update your system to ensure you have the latest packages.
sudo apt update && sudo apt upgrade -yStep 2: Install DirBuster
DirBuster can be installed using the following command:
sudo apt install dirbusterStep 3: Verify Installation
After installation, verify that DirBuster is available by running:
dirbusterIf the GUI opens, the installation was successful.
Using DirBuster for Scanning
Now that DirBuster is installed, let’s explore how to use it for scanning.
Step 1: Launch DirBuster
Run the following command to launch DirBuster:
dirbusterThis will open the GUI interface.
Step 2: Enter Target URL
-
In the "Target URL" field, enter the URL of the website you want to scan. For example:
http://example.com -
Ensure you have permission to test the target site, as unauthorized scanning is illegal.
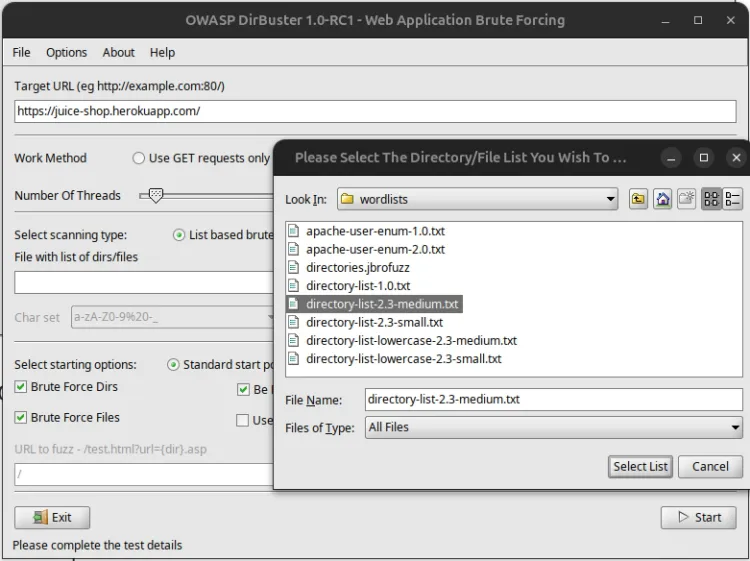
Step 3: Select a Wordlist
-
Choose a wordlist from the "Wordlist" section. Kali Linux provides several wordlists, typically located in the
/usr/share/dirbuster/wordlists/directory. -
Select an appropriate wordlist based on your scan requirements.
Step 4: Configure Options
-
Threads: Specify the number of threads for the scan. Increasing threads speeds up the scan but may overload the server.
-
File Extensions: Add specific file extensions to target (e.g.,
.php,.html,.txt). -
Recursive Scan: Enable this option to scan subdirectories.
Step 5: Start the Scan
Click on the "Start" button to begin the scan. DirBuster will start brute-forcing the directories and files on the target server.
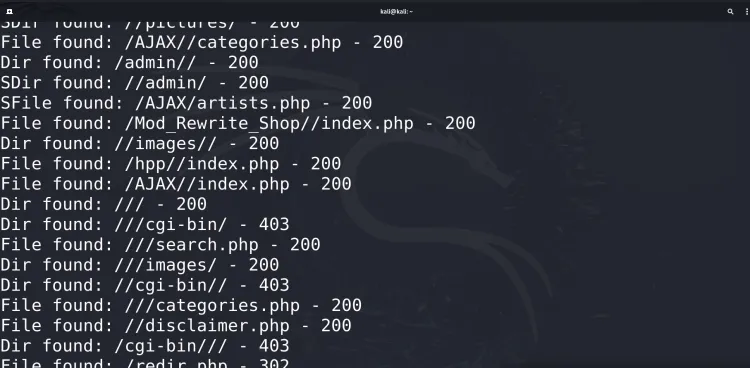
Step 6: Analyze Results
-
As the scan progresses, DirBuster will display found directories and files in real-time.
-
Review the results to identify sensitive or misconfigured directories that could pose security risks.
DirBuster Commands and Usage in CLI Mode
While DirBuster is primarily a GUI tool, it can also be run from the command line for automation or script integration. Here’s how to use it in CLI mode:
Basic Command Syntax
java -jar /usr/share/dirbuster/DirBuster.jar -H -u -l -t Example Command
java -jar /usr/share/dirbuster/DirBuster.jar -H -u http://example.com -l /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt -t 50Options:
-
-H: Enables headless mode (CLI). -
-u: Specifies the target URL. -
-l: Specifies the path to the wordlist. -
-t: Sets the number of threads for scanning.
Best Practices for Using DirBuster
-
Use Legal and Ethical Practices: Always obtain permission before scanning a website.
-
Optimize Wordlists: Use customized wordlists for better efficiency and accuracy.
-
Monitor Scan Intensity: Avoid overloading the target server by using appropriate thread settings.
-
Combine with Other Tools: Use DirBuster alongside other tools like Burp Suite and Nmap for comprehensive testing.
Conclusion
DirBuster is an essential tool for web application security testing, providing insights into hidden directories and files that could lead to vulnerabilities. With its user-friendly interface and powerful features, it’s an excellent choice for ethical hackers and penetration testers. By following the steps outlined above, you can effectively install and use DirBuster to enhance your security assessments.
Understanding the hidden structure of web servers can be critical for identifying and mitigating potential risks. Whether you’re a seasoned penetration tester or a beginner exploring ethical hacking tools, DirBuster offers an effective solution to reveal what lies beneath the surface.
FAQ:
1. What is DirBuster?
DirBuster is a tool used for brute-forcing directories and files on web servers, helping ethical hackers discover hidden resources on websites that might pose security risks.
2. Is DirBuster legal to use?
DirBuster is legal when used with the explicit permission of the website owner for ethical hacking and penetration testing purposes. Unauthorized use is illegal.
3. How do I install DirBuster on Kali Linux?
DirBuster can be installed via the terminal with the command sudo apt install dirbuster in Kali Linux. It may already be pre-installed in some versions of Kali.
4. Can DirBuster be used in headless mode?
Yes, DirBuster can be run from the command line in headless mode using the syntax: java -jar /usr/share/dirbuster/DirBuster.jar -H -u .
5. What types of wordlists can be used with DirBuster?
DirBuster supports various wordlists for scanning directories and files, including predefined lists in Kali Linux. You can also use custom wordlists for specific targets.
6. Can I scan for specific file extensions with DirBuster?
Yes, DirBuster allows you to target specific file extensions (e.g., .php, .txt, .html) to focus on certain types of files during the scan.
7. What is the purpose of the recursive scan feature in DirBuster?
The recursive scan option allows DirBuster to automatically scan subdirectories within discovered directories, helping to uncover additional hidden paths.
8. How do I choose the right wordlist for DirBuster?
Select a wordlist based on your target’s structure and requirements. Kali Linux provides several options, and custom wordlists may improve scan effectiveness.
9. Can DirBuster overload a web server?
Yes, using too many threads or aggressive scanning can overload a server. It's important to monitor and adjust the number of threads to avoid disrupting services.
10. What should I do with the results from DirBuster?
Review the discovered directories and files for sensitive information or misconfigurations that could be potential security risks. Use this information for further penetration testing.












![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)

![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)









