BlackEye Phishing Tool: Features, Installation, and Best Practices
BlackEye is an open-source phishing simulation tool widely used in ethical hacking and cybersecurity training. It helps simulate phishing attacks by hosting realistic phishing pages for platforms like Facebook, Instagram, and Google. By leveraging tunneling services like Ngrok, BlackEye exposes these pages online and captures entered credentials in real time. This tool is intended for ethical purposes, such as training and awareness campaigns, and must always be used with proper authorization.

In the realm of ethical hacking and penetration testing, phishing simulation tools are essential for assessing the security awareness of users and the resilience of an organization against social engineering attacks. Among the most prominent tools is BlackEye, an open-source phishing tool known for its simplicity and effectiveness in crafting phishing pages.
This blog provides a comprehensive guide to BlackEye, detailing its features, installation, usage, and best practices. This guide is for educational purposes only and is intended for ethical use in a controlled environment with proper authorization.
What is BlackEye?
BlackEye is a phishing simulation tool designed to create phishing pages that mimic popular websites and platforms. It is widely used in cybersecurity training, awareness campaigns, and penetration testing. By hosting a phishing page and generating a publicly accessible link, it allows ethical hackers to test how users respond to phishing attempts.
Warning: Unauthorized use of BlackEye for malicious purposes is illegal and punishable under cybersecurity laws. Always obtain consent before conducting tests.
Key Features of BlackEye
-
Pre-configured Templates
BlackEye includes phishing page templates for major platforms such as Facebook, Instagram, Twitter, Google, and LinkedIn. -
Tunneling Services
Integrates with tunneling services like Ngrok, Cloudflared, and LocalhostRun to host phishing pages on publicly accessible URLs. -
Real-Time Credential Capture
Captures credentials entered on the phishing pages and displays them in the terminal in real time. -
Cross-Platform Compatibility
Works on most Linux-based operating systems, including Kali Linux, Ubuntu, and Parrot OS. -
Customizable and Extendable
Allows users to modify or add custom templates to target other platforms as needed.
Why Use BlackEye for Ethical Hacking?
-
Phishing Awareness
Simulates real-world phishing attacks to educate users on identifying phishing attempts. -
Security Assessments
Tests how systems and users respond to phishing links and credentials theft attempts. -
Training and Development
Helps cybersecurity professionals understand phishing tactics and develop countermeasures. -
Easy to Use
BlackEye’s simple interface makes it accessible even for beginners in cybersecurity.
How to Install BlackEye
Follow these steps to install and set up BlackEye on a Linux system.
Step 1: Update Your System
Ensure your system is updated to avoid compatibility issues:
sudo apt update && sudo apt upgrade -y
Step 2: Clone the BlackEye Repository
Download BlackEye from its official GitHub repository:
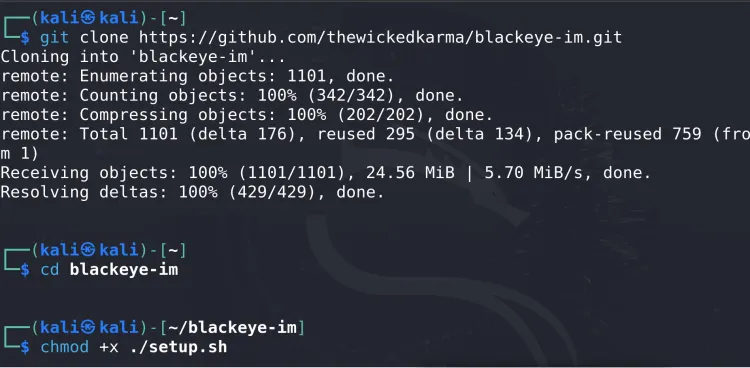
git clone https://github.com/thewickedkarma/blackeye-im.git
Step 3: Navigate to the BlackEye Directory
Move into the directory where BlackEye has been downloaded:
cd blackeye-im
Step 4: Grant Execute Permissions
Ensure the script has execute permissions:
chmod +xblackeye.sh
Step 5: Install Dependencies
Install required tools like PHP, curl, and unzip:
sudo apt install curl php unzip -y
Step 6: Run the Script
Launch BlackEye with the following command:
./blackeye.sh
This starts the tool and displays a menu of phishing templates and options.
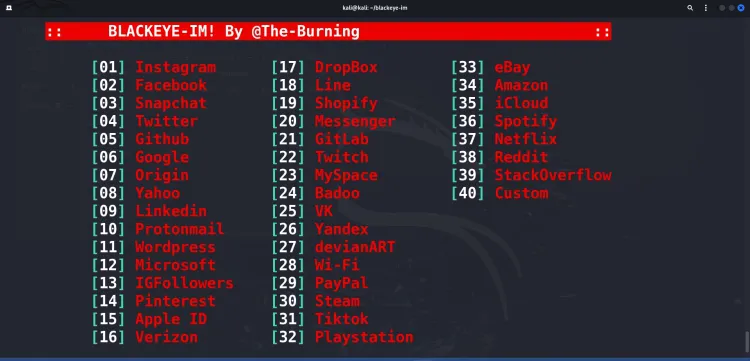
How to Use BlackEye
Once installed, follow these steps to simulate a phishing attack ethically:
Step 1: Select a Platform
Choose a platform from the menu (e.g., Facebook, Instagram, Twitter). Each platform corresponds to a number.
For example, to create a phishing page for Instagram, type the assigned number and press Enter.
Step 2: Choose a Tunneling Service
BlackEye uses tunneling services to expose phishing pages to the internet. Options include Ngrok and Cloudflared:
- If Ngrok is installed, BlackEye uses it.
- If not, BlackEye will download and configure it automatically.
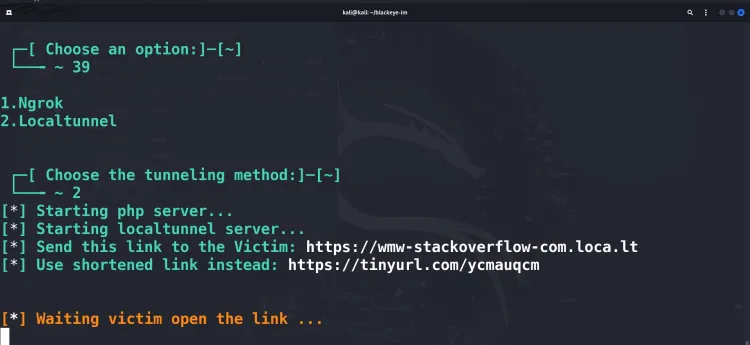
Step 3: Share the Generated Link
BlackEye generates a public URL. Share this link with your test subjects (with their consent).
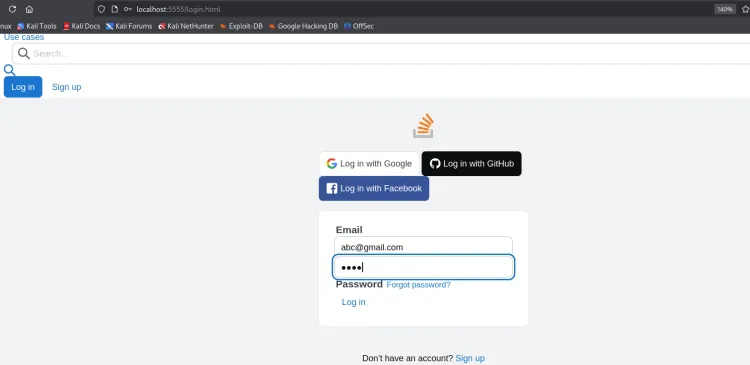
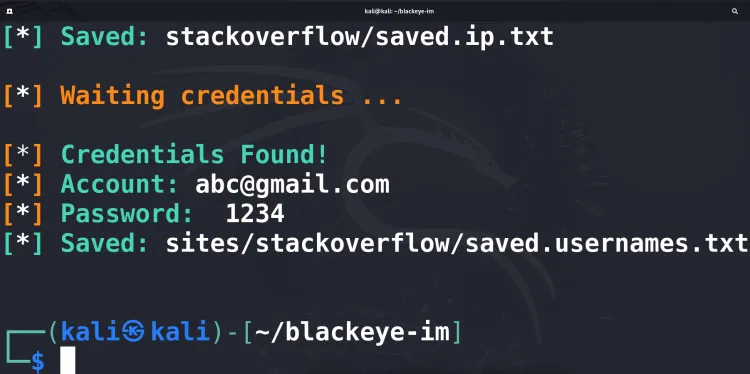
Step 4: Monitor the Results
BlackEye captures credentials entered on the phishing page and displays them in real-time in the terminal.
For example:
[+] Username: testuser
[+] Password: testpassword123 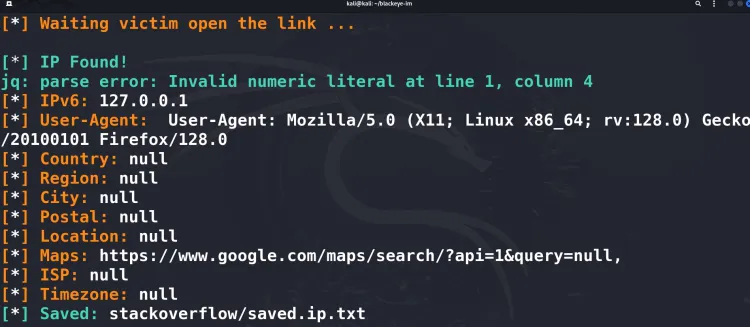
Best Practices for Using BlackEye
-
Obtain Explicit Permission
Always get written permission before conducting phishing simulations. -
Use Custom Templates
Modify templates to closely mimic the target’s legitimate website for better accuracy. -
Educate After Testing
Share insights and educate users on identifying phishing attempts post-simulation. -
Avoid Overloading Systems
Use BlackEye responsibly to avoid system overload. -
Integrate with Training Programs
Combine BlackEye simulations with awareness sessions for better impact.
Common Issues and Solutions
-
Error:
Permission Denied
Ensure execute permissions using:chmod +xblackeye.sh -
Ngrok Not Working
Verify Ngrok is installed and properly configured. Reinstall if necessary. -
Script Fails to Run
Check for missing dependencies (PHP, curl, unzip) and reinstall using:sudo apt install curl php unzip -y
Conclusion
BlackEye is a versatile tool for ethical hackers to simulate phishing attacks and enhance security awareness. Its ability to create convincing phishing pages and capture credentials in real-time makes it invaluable for penetration testers. However, always use BlackEye ethically and with permission to avoid legal consequences.
By following this guide, you can install and use BlackEye effectively to assess and improve the cybersecurity posture of organizations. Phishing awareness is a crucial component of modern cybersecurity, and tools like BlackEye are pivotal in building resilient systems and educated users.
Disclaimer: This blog is for educational purposes only. Misuse of BlackEye is illegal and unethical. Always adhere to ethical hacking principles and cybersecurity laws.
FAQ:
What is BlackEye?
BlackEye is an open-source phishing tool designed to simulate phishing attacks by hosting phishing pages and capturing credentials for educational and ethical purposes.
Is BlackEye legal to use?
Yes, but only in controlled environments with explicit authorization. Unauthorized use is illegal and unethical.
Which platforms can BlackEye simulate?
BlackEye supports phishing page templates for platforms like Facebook, Instagram, Twitter, Google, LinkedIn, and more.
What are the prerequisites for running BlackEye?
You need a Linux-based operating system and dependencies like PHP, curl, and unzip installed.
Does BlackEye work on Windows?
BlackEye is primarily designed for Linux systems. It may require additional setup or compatibility layers to run on Windows.
What are tunneling services, and why are they used?
Tunneling services like Ngrok and Cloudflared expose local phishing pages to the internet, making them accessible via public URLs.
Can I add custom templates in BlackEye?
Yes, BlackEye allows you to modify or add custom phishing page templates to target additional platforms.
What precautions should I take while using BlackEye?
Always obtain consent, use it responsibly in a controlled environment, and educate users about phishing after simulations.
What should I do if BlackEye doesn’t run correctly?
Ensure dependencies like PHP and curl are installed. Also, check for permission issues and reassign execution permissions using chmod +x blackeye.sh.
What are the ethical applications of BlackEye?
BlackEye is used in cybersecurity training, phishing awareness programs, and penetration testing to improve security posture and educate users about phishing risks.












![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)

![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)









