Ansible for Cybersecurity | Automating Security Tool Installation and Scans
Ansible is a powerful tool that helps automate many aspects of ethical hacking, including tool deployment, system configuration, and vulnerability scanning. In this guide, we walked through the process of installing Ansible on Kali Linux, writing playbooks, and executing them in real-time scenarios such as deploying Nmap and running security scans across multiple machines. This automation can save a lot of time and reduce errors, allowing ethical hackers to focus on critical tasks like analysis and remediation.

Ansible, an open-source IT automation tool, has revolutionized the way tasks are executed in cybersecurity and IT management. By simplifying repetitive tasks, ensuring configuration consistency, and enabling efficient management of multiple systems, Ansible is widely utilized in the cybersecurity domain. In this blog, we explore the use of Ansible in cybersecurity, focusing on automating security tool installations and tasks locally on a Kali Linux system.
What is Ansible?
Ansible is an agentless automation tool designed for IT operations such as configuration management, application deployment, and task automation. It uses simple YAML-based playbooks to define and execute tasks, making it easy for users to manage systems without writing complex code.
Why Use Ansible in Cybersecurity?
-
Consistency: Ensures uniform deployment of configurations and tools across multiple systems.
-
Efficiency: Automates time-consuming tasks like tool installation and configuration.
-
Agentless Architecture: Eliminates the need for additional software on target systems.
-
Scalability: Easily manages numerous systems simultaneously.
-
Auditing and Reporting: Logs and outputs make it easy to audit actions and track changes.
Use Case: Automate Security Tool Installation Locally
For cybersecurity professionals, automating the installation and configuration of tools like Nmap, Wireshark, and Nikto can save valuable time. Below, we outline how Ansible can be used locally on a Kali Linux system to automate these tasks.
Step 1: Create a Local Inventory File
Ansible can target the local machine by specifying localhost in an inventory file.
-
Create an Inventory File:
nano ~/local_inventory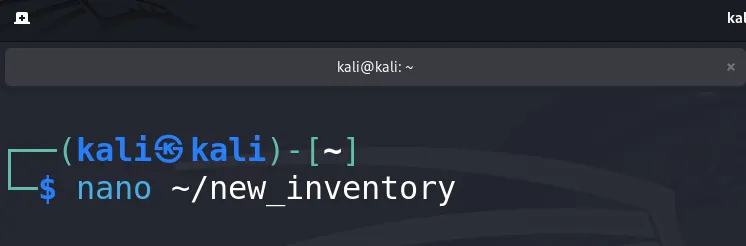
-
Add Localhost:
[local] localhost ansible_connection=local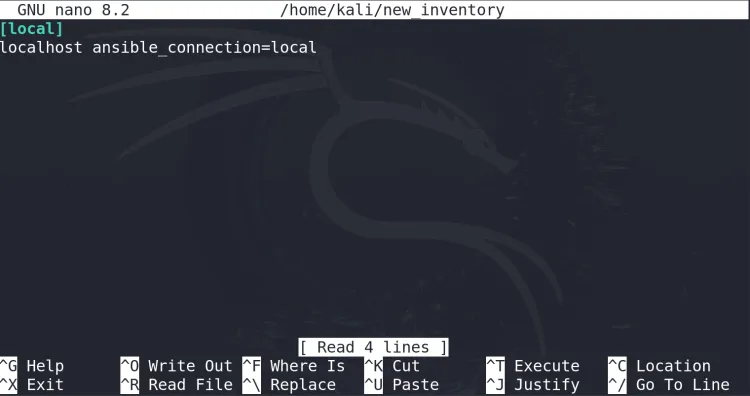
-
Save and Exit: Save the file and exit (
Ctrl + X, thenYto confirm).
Step 2: Write a Playbook for Local Automation
A playbook defines the tasks to be executed. Here, we create one to install multiple security tools on the local system.
-
Create a Playbook:
nano install_tools.yml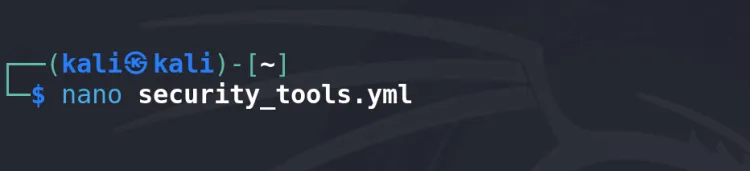
-
Write the Playbook:
--- - name: Install security tools locally hosts: local become: yes tasks: - name: Install Nmap apt: name: nmap state: present - name: Install Wireshark apt: name: wireshark state: present - name: Install Nikto apt: name: nikto state: present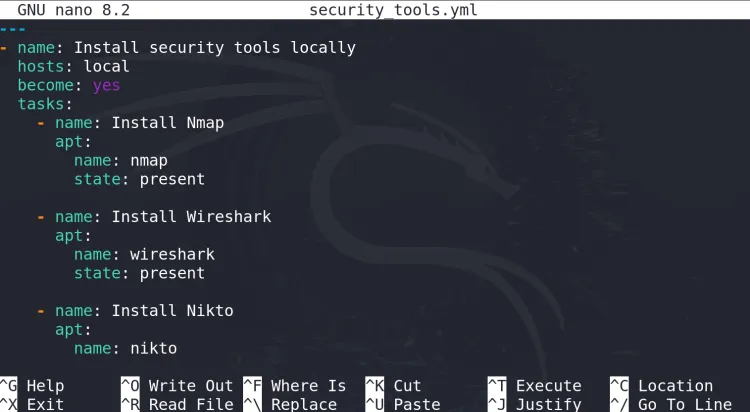
-
Save and Exit: Save the playbook and exit the editor.
Step 3: Run the Playbook Locally
Now, execute the playbook to install the tools on your Kali Linux system.
-
Run the Playbook:
ansible-playbook -i ~/local_inventory install_tools.yml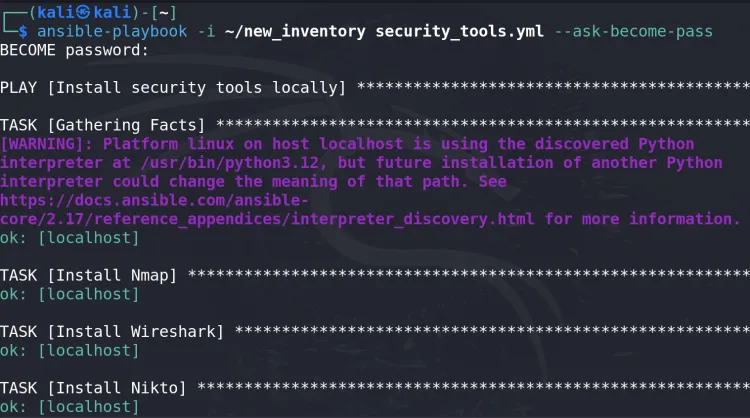
-
Observe the Output: Ansible will execute the tasks and display the status for each task in the terminal.
Step 4: Verify the Installation
Once the playbook completes, verify that the tools are installed:
-
Check Nmap:
nmap --version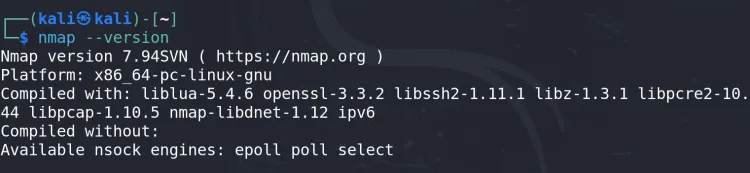
-
Check Wireshark:
wireshark --version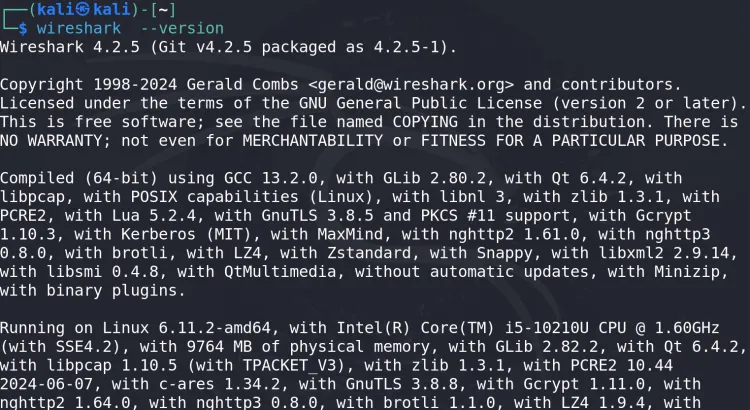
-
Check Nikto:
nikto --version
Step 5: Extend the Playbook (Optional)
You can extend the playbook to automate additional tasks, such as configuring tools or running scans. For instance, automate an Nmap scan on your localhost and save the output to a file.
-
Modify the Playbook:
- name: Run an Nmap scan command: "nmap -T4 -A -v localhost -oN ~/nmap_scan_results.txt" -
Re-run the Playbook:
ansible-playbook -i ~/local_inventory install_tools.yml -
Check the Scan Results: View the Nmap scan results:
cat ~/nmap_scan_results.txt
Benefits of Using Ansible Locally
-
Simplicity: No need for remote connections or SSH setups.
-
Customizability: Easily add or modify tasks to meet specific requirements.
-
Resource Efficiency: Uses the local machine’s resources effectively.
-
Enhanced Security: Direct control over sensitive operations without exposing them to a network.
Best Practices for Using Ansible in Cybersecurity
-
Use Version Control: Track changes to your playbooks with Git.
-
Test Playbooks Locally: Verify functionality before deploying to remote systems.
-
Enable Logging: Keep logs of Ansible executions for auditing.
-
Secure Sensitive Data: Use Ansible Vault to encrypt sensitive variables.
-
Update Regularly: Ensure Ansible and its dependencies are up-to-date.
Conclusion
Ansible is a powerful tool for automating tasks in cybersecurity. By automating the installation and configuration of security tools on your local machine, you can save time and reduce errors. Once familiar with local automation, you can extend these practices to manage remote systems and scale your cybersecurity operations efficiently. Embrace Ansible to streamline your workflows and focus on tackling more critical challenges in the cybersecurity landscape.
FAQs
-
What is Ansible used for? Ansible is used for automating IT tasks like software installation, system configuration, and application deployment.
-
Is Ansible agentless? Yes, Ansible is agentless and works over SSH without requiring additional software to be installed on target machines.
-
What is a playbook in Ansible? A playbook in Ansible is a YAML file that defines the tasks to be executed on target machines.
-
How does Ansible ensure security? Ansible uses SSH for secure communication with target nodes, avoiding the need for additional agents and open ports.
-
Can Ansible be used for vulnerability management? Yes, Ansible can be used to patch systems and deploy security updates, helping with vulnerability management.
-
What are Ansible modules? Modules in Ansible are pre-built scripts that perform specific tasks, like installing software or configuring network settings.
-
How do I create an inventory file in Ansible? An inventory file is a text file where you list the IP addresses or hostnames of the target machines that Ansible will manage.
-
Can Ansible be used in penetration testing? Yes, Ansible can automate the deployment and execution of penetration testing tools across multiple systems.
-
How do I encrypt sensitive data in Ansible? You can use Ansible Vault to encrypt sensitive data, such as passwords or API keys, in your playbooks.
-
Is Ansible difficult to learn? No, Ansible is easy to learn due to its simple YAML syntax and extensive documentation.











![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)



![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)







